Secure Connect & SASE Evolution: When "Meet You Where You Are" Becomes Strategy
Cisco's SASE strategy evolved from "our way or the highway" to "we'll meet you where you are"—supporting single-vendor, dual-vendor, and hybrid deployments. That shift reveals more about market reality than any product launch. Here's why pragmatic flexibility might be their smartest move.
Part of "Building Toward Amsterdam" - A public learning exercise ahead of Cisco Live EMEA 2026
Read the series:
- Why I'm Making the Bull Case
- Silicon One: Cisco's Ethernet Bet
- Hypershield: Security in the Data Path
- Splunk: The $28B Data Operating System
- AgenticOps & AI Canvas: When AI Understands Your Network
Cisco's SASE message has evolved from competitive rigidity to collaborative pragmatism—and that shift reveals more about their strategy than any product launch could.
Here's what I find fascinating: Five years ago, Cisco's SASE positioning was essentially "our way or the highway." You deployed Cisco SD-WAN with Cisco security, managed through Cisco dashboards. Period. The pitch was single-vendor purity—all Cisco, full stack integration, no compromises.
Today? Cisco's SD-WAN officially integrates with Zscaler, Cloudflare, Netskope, Palo Alto, and Microsoft. They publish reference architectures for dual-vendor SASE. They've built a modular SSE solution (Cisco Secure Access) specifically designed to work alongside third-party networking.
That's not just product roadmap evolution. That's strategic maturity—acknowledging that winning in SASE means meeting customers where they are, not demanding they come to you.
Let me show you why this pragmatic turn is actually more interesting than the competitive narrative Cisco used to tell, what it signals about the market, and how it positions them going forward.
The SASE Dream: Elegant in Theory, Challenging in Practice
Let's start with what Gartner envisioned when they coined "SASE" in 2019.
The concept was elegant: converge networking (SD-WAN) and security (SSE: Secure Service Edge) into a unified, cloud-delivered service. Instead of separate teams managing separate tools with separate policies, you'd have one architecture that securely connected users, devices, and applications—regardless of location.
The promise:
- Unified management (one dashboard, one policy engine)
- Consistent security enforcement (whether users are in the office, at home, or on the road)
- Simplified operations (fewer vendors, fewer integration headaches)
- Better performance (security enforcement at the edge, closer to users)
The reality? Most enterprises weren't ready to rip out their existing infrastructure and replace everything with a single-vendor SASE solution—no matter how elegant the architecture.
They had existing SD-WAN deployments. They had security tools that worked. They had teams with specialized expertise in specific products. And they had budgets, contracts, and political realities that made "start over with unified SASE" impractical.
Enter market fragmentation.
Market Fragmentation: Why No Single Vendor Ran Away With It
By 2023, the SASE market had fractured instead of consolidating.
Pure-play SSE vendors like Zscaler, Netskope, and Cloudflare leaned hard into their security strength — promising to work with any SD-WAN and positioning themselves as the Switzerland of security.
Meanwhile, networking vendors like Cisco and Palo Alto argued that owning both sides of the equation — connectivity and security — was the only path to a truly unified experience.
Customers, of course, didn’t follow either script. They mixed and matched — pairing SD-WAN from one vendor with security from another, often based on existing contracts or team expertise. No one ran away with the market.
Zscaler remained the SSE reference point, unmatched in scale but still without a full SD-WAN story. Palo Alto offered a balanced portfolio with Prisma Access and its CloudGenix acquisition, but the operational integration still feels more promised than proven. Fortinet captured the mid-market with cost-effective breadth, yet enterprise buyers still question its scalability. And Cisco — caught early in its single-vendor stance — has since recognized that flexibility is the more durable advantage.
The net effect: flexibility, not purity, started winning deals. The vendors who enabled coexistence earned revenue even when they didn’t win the whole stack.
Cisco's Pragmatic Pivot: Expanding the Tent Through Integration
Cisco's initial SASE strategy was clear: single-vendor simplicity was the way to go. The vision was compelling—a fully integrated stack from a single provider, eliminating the complexity of managing multiple vendors. But there was one problem: the market wasn't buying it.
Customers, it turned out, valued flexibility more than single-vendor purity. They had existing investments in best-of-breed solutions they weren't willing to rip and replace. They wanted the freedom to mix and match components based on their specific needs. And they balked at the idea of being locked into a single vendor's stack, no matter how well-integrated it claimed to be.
Faced with this reality, Cisco made a pragmatic pivot. Instead of doubling down on the single-vendor message, they embraced the dual-vendor reality. They built robust integrations with leading SSE vendors like Zscaler, Cloudflare, and Netskope.
They created a flexible architecture that could accommodate a range of deployment models. And they shifted their messaging from "our way or the highway" to "we'll meet you where you are."
This wasn't a capitulation; it was a smart strategic move. By supporting both single-vendor and dual-vendor approaches, Cisco expanded its addressable market. They could now compete for pure-play SD-WAN deals, standalone SSE opportunities, and full SASE stack replacements. They could meet customers where they were in their SASE journey, rather than demanding they start from scratch with an all-Cisco solution.
In a fragmented market, this flexibility is a competitive advantage. It allows Cisco to capture a larger share of the overall SASE opportunity, even if they don't win every single component of every deal. It positions Cisco as a pragmatic partner that understands the realities of enterprise IT, rather than a dogmatic vendor pushing a one-size-fits-all approach.
To fully capitalize on the opportunity, Cisco needs to deliver on the promise of architectural flexibility without operational complexity. They need to prove that their dual-vendor integrations are not just marketing slideware, but robust, enterprise-grade solutions. And they need to show that their single-vendor offerings are truly differentiated, not just bundled for the sake of bundling.
That’s the opportunity—and the test that Cisco's pragmatic SASE pivot presents. By expanding the tent through integration, they've positioned themselves to compete across the full spectrum of SASE deployment models.
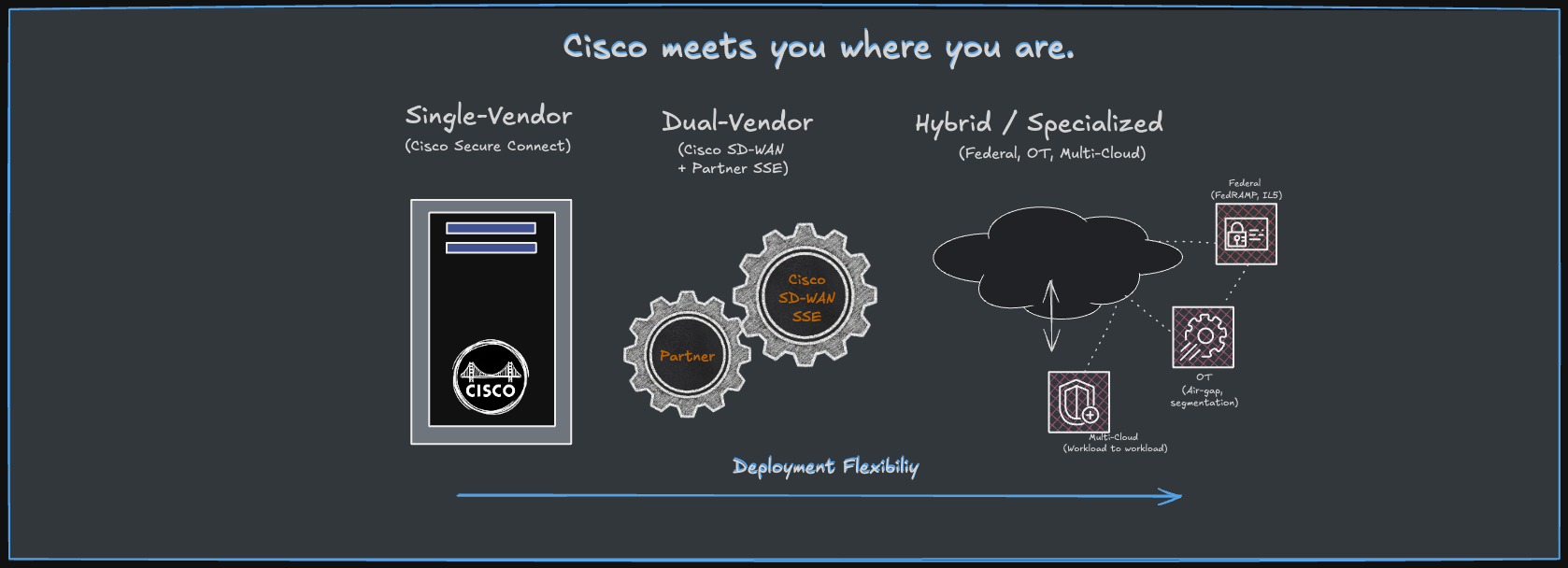
Here’s the spectrum that shift unlocks:

But the proof will be in the execution. Can they deliver the operational simplicity of a single-vendor solution while still supporting the architectural flexibility the market demands? The answer will determine whether Cisco's SASE pivot is truly pragmatic or merely expedient.
The Architecture: How Cisco Actually Makes This Work
Let's get specific about how the flexible approach translates to real deployments, because "we support everything" can be marketing hand-waving if the integration isn't real.
Unified SASE: The Single-Vendor Path
Cisco+ Secure Connect combines:
- Meraki SD-WAN for intelligent WAN connectivity
- Cisco Secure Access (SSE) for cloud security
- Unified management through the Meraki Dashboard
- Shared policy engine across networking and security
The key architectural choices:
- Single console: Meraki Dashboard becomes the primary interface. You configure SD-WAN and SSE policies in one place, with tight integration—not separate dashboards linked by SSO.
- Unified telemetry: Network and security data flow into a common data plane (Splunk integration provides the correlation layer we discussed in BTA-2504).
- Consistent policy enforcement: Identity-based policies apply across both networking and security decisions. A user's access rights, device posture, and risk profile inform both SD-WAN path selection and security filtering.
This is what single-vendor SASE is supposed to look like: architectural unity, not just co-marketing.
Modular SSE: The Flexible Path
Cisco Secure Access as a standalone SSE works with:
- Cisco Catalyst SD-WAN (the Viptela-based enterprise SD-WAN)
- Third-party SD-WAN (Fortinet, VMware, HPE Aruba, or any IPsec-capable WAN edge)
- Direct internet access without SD-WAN (for cloud-first organizations)
Six SSE components:
- Secure Web Gateway (SWG): URL filtering, malware protection
- Cloud Access Security Broker (CASB): SaaS security posture management, shadow IT discovery
- Data Loss Prevention (DLP): Content inspection and policy enforcement
- Zero Trust Network Access (ZTNA): Identity-based access to private applications
- Firewall as a Service (FWaaS): Stateful inspection, IPS/IDS, threat prevention
- DNS Security: Recursive DNS protection (Cisco's legacy Umbrella strength)
These SSE capabilities are delivered from Cisco's global cloud infrastructure, with policy enforcement happening at the edge—close to users—for performance and consistent protection.
The dual-vendor integration is where it gets interesting.
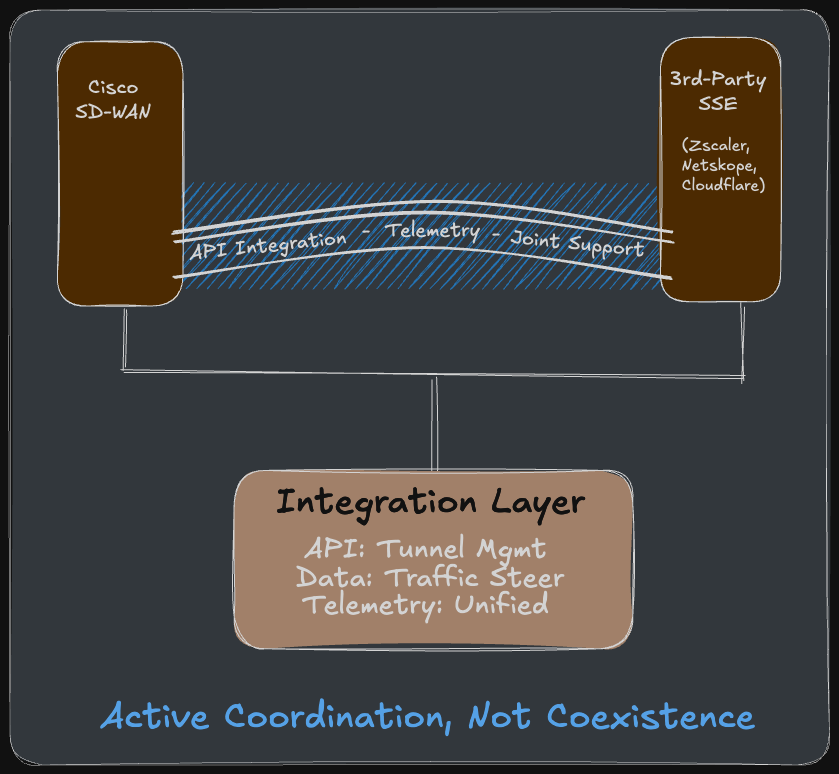
Dual-Vendor SASE: The Integration Reality
When Cisco SD-WAN integrates with Zscaler (or Cloudflare, Netskope, Palo Alto), here's what actually happens:
Automated Tunnel Provisioning: Cisco SD-WAN Manager uses APIs to automatically create IPsec or GRE tunnels between branch edge devices and the third-party SSE cloud. No manual configuration. The SD-WAN orchestrator talks to Zscaler's API, provisions tunnels, and maintains them dynamically as branches come online.
Intelligent Traffic Steering: Cisco SD-WAN uses application-aware routing to steer traffic intelligently:
- Internet-bound traffic → Zscaler for security inspection
- SaaS traffic → Direct to cloud, with Zscaler inline for security
- Private app traffic → Encrypted back to data center or via ZTNA
The SD-WAN understands application context (which app, which user, which device posture) and makes routing decisions accordingly—without requiring users to understand the underlying topology.
Unified Troubleshooting: When something breaks (and it always does), operations teams need to see the full path:
- SD-WAN tunnel status
- SSE inspection latency impact
- Recent policy changes (either side)
Cisco's integration provides telemetry correlation—SD-WAN visibility combined with SSE logs—so troubleshooting doesn't require logging into completely separate systems and manually correlating timestamps.
This is the difference between "coexistence" (both products work separately) and "integration" (they actively coordinate).
The Edge Cases That Expand the Market
Federal & National Security.
Air-gap, FedRAMP tiers, IL5—these environments punish cloud-only assumptions. Cisco’s mix of Secure Access for Government + SD-WAN + air-gapped options plays where pure SSE can’t.
Operational Technology (OT).
Plants and grids need segmentation, legacy protocol support, and sometimes zero internet. Cisco’s hybrid: SD-WAN on-prem for OT, Secure Connect for IT, policy at the boundary.
Multicloud Reality.
It’s not just users→SaaS. It’s site↔cloud and cloud↔cloud. SD-WAN for paths, Secure Access for users, Multicloud Defense for workload↔workload closes the triangle.
Takeaway: Flexibility matters most where constraints are non-negotiable.
The Competitive Landscape: Where Cisco Stands
Let's be honest about where Cisco is winning, where they're behind, and why the pragmatic strategy matters.
Zscaler: The SSE Leader Playing Catch-Up on Networking
Zscaler's Strength: Best-in-class SSE with massive scale, mature ZTNA, and the "Switzerland" positioning that lets them work with any SD-WAN vendor.
Zscaler's Challenge: They don't have SD-WAN. They partnered with networking vendors for years, but Gartner's push toward single-vendor SASE created pressure to add networking themselves. In 2024-2025, Zscaler started building their own SD-WAN capabilities—but it's early, and it risks alienating their SD-WAN partners.
Cisco's Counter: "Use Zscaler SSE if you prefer. We integrate beautifully. But if you want single-vendor simplicity eventually, we have the full stack ready whenever you're ready to consolidate."
Palo Alto Networks: The Balanced Competitor
Palo Alto's Strength: Strong in both SD-WAN (acquired CloudGenix) and SSE (Prisma Access). Genuinely competitive single-vendor SASE story.
Palo Alto's Challenge: Integration maturity. They acquired their way into SASE (CloudGenix for SD-WAN, multiple security acquisitions for SSE), and the unified story is still maturing. Operations teams report that Prisma Access and Palo Alto SD-WAN still feel like separate products in practice.
Cisco's Counter: "We've been integrating Meraki and Umbrella for years. Our single-vendor SASE is operationally mature, not just architecturally plausible."
Fortinet: The SMB and Mid-Market Challenger
Fortinet's Strength: Cost-effective, broad security portfolio, strong in SMB and mid-market where "good enough and affordable" wins.
Fortinet's Challenge: Enterprise credibility and scale. Large enterprises question whether Fortinet's SASE can handle their complexity and global footprint.
Cisco's Counter: "We operate at enterprise scale. When you need to deploy SASE across 5,000 sites in 80 countries with complex compliance requirements, we've done it before."
The Market Reality
According to Dell’Oro Group, the global SASE market grew 17 percent year-over-year to $2.6 billion in Q1 2025—yet no vendor commands more than 20 percent of the total share. Zscaler continues to lead SSE revenue, while Cisco and Palo Alto remain closely matched in overall SASE share. The result is the same story as years prior: a market expanding fast but refusing to consolidate.
That's strategic hedging, not weakness.
Source: Dell’Oro Group, “SASE Market Sees 17% 1Q Revenue Increase,” May 2025
Execution Readiness: What's Shipping vs. What's Still Roadmap
Let's be clear about maturity, because SASE marketing is rife with vaporware.
Shipping Now (Q4 2025):
Cisco+ Secure Connect (Unified SASE): Generally available with Meraki SD-WAN and Cisco Secure Access SSE, managed through Meraki Dashboard. This is mature—customers are deploying at scale.
Cisco Secure Access (Standalone SSE): Generally available, FedRAMP Moderate authorized for government, works with Cisco SD-WAN and third-party networking.
Third-Party SSE Integrations: Zscaler, Cloudflare, Netskope integrations with Cisco SD-WAN are shipping, documented, and supported. Reference architectures and deployment guides are available.
AT&T SASE with Cisco: Just announced (August 2025)—AT&T becomes the first North American service provider offering single-vendor SASE built on Cisco technology. This is a managed service play that extends Cisco's reach into enterprises that want service provider management.
In Progress (2026):
FedRAMP High Authorization: Cisco Secure Access is pursuing FedRAMP High for agencies with more stringent requirements. This opens higher-classification government workloads.
DoD Impact Level 5 (IL5): Required for classified national security systems. Cisco's building this, but it's roadmap—not shipping today.
Air-Gapped SASE Deployments: The vision of fully disconnected SASE for national security environments. Cisco's proven the concept with Webex air-gap, but extending it to SASE requires significant engineering.
Enhanced Multicloud Defense Integration: Deeper integration between SASE (user access) and Multicloud Defense (workload protection) for comprehensive zero-trust across users and applications.
The Honest Assessment: The flexible SASE approach is shipping and mature. The specialized federal/OT/air-gap capabilities are in progress, with some components available and others still being built.
Amsterdam Preview: What I'm Watching For
At Cisco Live Amsterdam 2026, the real test of Cisco’s pragmatic SASE strategy isn’t in new features—it’s in proof. I’m watching for real deployments, real data, and real differentiation:
- Customer stories: Enterprises running dual-vendor SASE at scale, not just slideware.
- Ecosystem proof: Service providers and integrators building on Cisco’s stack.
- Operational metrics: Measurable efficiency—MTTR, ticket reduction, migration patterns.
- Regulated edge cases: Federal and OT customers showing it works under real constraints.
- Messaging clarity: Does Cisco lean into flexibility or drift back to single-vendor purity?
If those signals are clear, “meet you where you are” becomes more than a tagline—it becomes execution.
Strategic Implications: SASE's Place in Cisco's Transformation
Step back and look at where SASE sits in Cisco's broader strategy:
The connectivity layer is the foundation, but it only works at scale when unified intelligence flows through the entire stack:
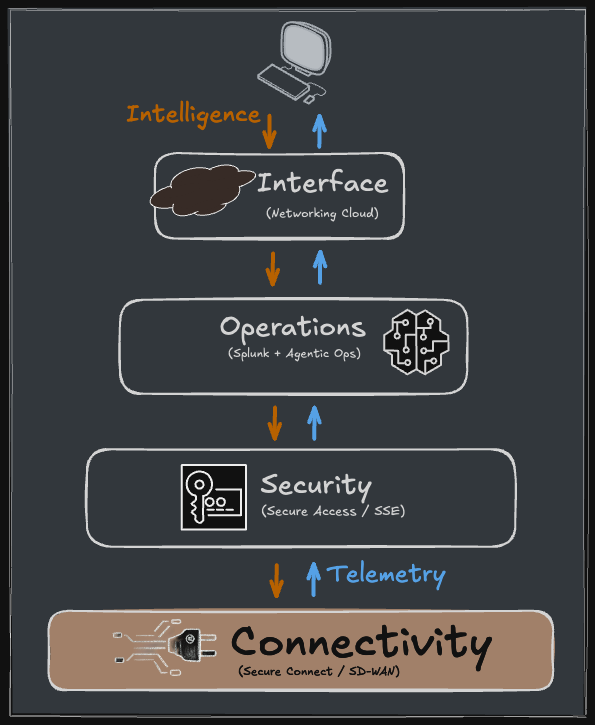
Secure Connect provides the secure connectivity fabric for distributed users and sites
Cisco Secure Access (SSE) enforces security policies at the edge, close to users
Networking Cloud (which we'll dive into in the next post) provides unified management across SD-WAN, Meraki, and Catalyst
Splunk unifies telemetry from SASE, network, and security for correlation and intelligence
AgenticOps agents use that unified telemetry to automate troubleshooting and remediation across SASE infrastructure
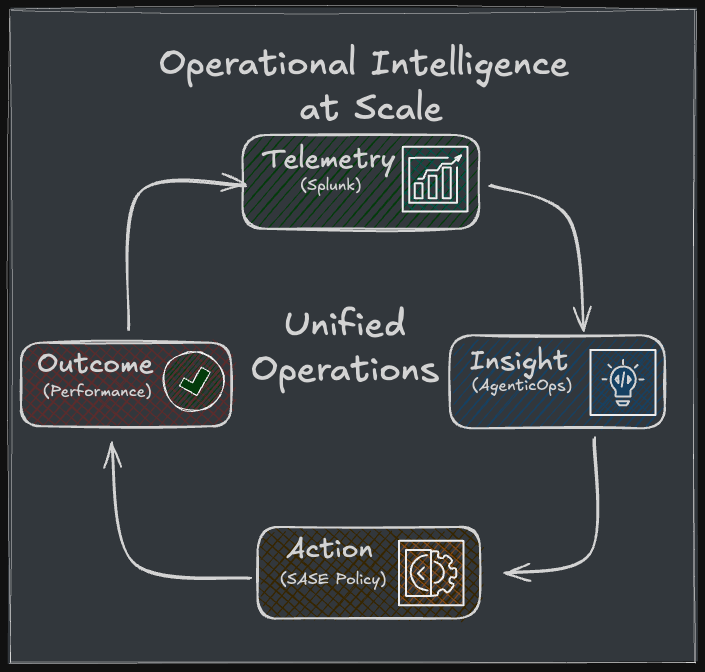
t's a stack. SASE is the connectivity and security layer. The operational intelligence (Splunk, AgenticOps, Networking Cloud) makes it manageable at scale.
But here's the key insight: Cisco's pragmatic SASE approach—supporting flexible deployment models—only works if the operational layer is genuinely unified. If dual-vendor SASE creates operational complexity that cancels out the flexibility benefits, customers won't adopt it.
That's why the Splunk integration and Networking Cloud unification matter so much. They're what makes "flexible SASE" operationally viable rather than just architecturally possible.
The Bottom Line
Here's what Cisco's actually saying with their SASE evolution: the market isn't going to consolidate to single-vendor as fast as Gartner predicted, and winning means meeting customers where they are—not demanding they come to us.
The strategic bet is that flexibility expands the addressable market more than single-vendor purity differentiates. And the operational bet is that unified management, correlation, and automation can make dual-vendor deployments as operationally simple as single-vendor ones.
If Cisco executes on both—flexible deployment options AND unified operational layer—they're positioned to capture revenue across multiple SASE patterns: single-vendor, dual-vendor, hybrid, federal, OT.
If they fail on operational unification, flexibility becomes operational complexity, and the pragmatic strategy backfires.
That's the test. Amsterdam will show us which outcome is materializing.
But here's what I find most interesting: the shift from "our way or highway" to "we'll meet you where you are" required organizational maturity. It required acknowledging that customers weren't wrong to want best-of-breed choices. It required building real integrations with competitors instead of just competing against them.
That's not capitulation. That's strategic evolution.
And in a market as fragmented as SASE, it might be the smartest competitive move Cisco's made.
Your Take?
Are you deploying SASE in your environment—single-vendor, dual-vendor, or something else? What drove that decision? Was it technical, political, or just "this is what we already had deployed"?
And if you're running dual-vendor SASE (Cisco SD-WAN with third-party SSE, or vice versa): Does the integration actually work, or is it still operationally painful?
I'm especially curious about edge cases: federal customers, OT environments, air-gapped scenarios. Are Cisco's specialized capabilities for these environments real, or still mostly roadmap?
I'm headed to Amsterdam to see how much of the flexible SASE vision has shipped versus how much is still positioning. If you're planning to be there—or if you're already running Cisco SASE in production—I'd love to hear what you're seeing.
Sources and Further Reading:
Cisco Official Resources:
- Cisco Secure Connect (SASE Solution)
- Cisco Secure Access (SSE Solution)
- Cisco SD-WAN + Third-Party SSE Integrations
- AT&T SASE with Cisco Announcement
- Cisco Secure Access for Government (FedRAMP)
Industry Analysis:
- Dell’Oro Group: SASE Market Sees 17% 1Q Revenue Increase (May 2025)
- SDxCentral: Cisco SASE Integration Progress
- Cisco Blog: More SASE Options with Third-Party SSE
Federal and OT Security:
- Federal News Network: IT-OT Convergence in Federal Networks
- FedTech Magazine: Air-Gapped Cloud for DOD
Next in the series: Security Cloud Control and Identity—how Duo plus Cisco Identity Intelligence delivers continuous identity security, and whether the unified control plane for security actually reduces operational burden in practice.
About this series: I'm building toward Cisco Live Amsterdam in February 2026 by making sense of Cisco's biggest strategic moves. This is part learning exercise, part knowledge sharing. I'll be hosting the Cisco Live broadcast again this year, and I want to show up with a clear understanding of the storylines Cisco's building. If something here resonates—or if you think I'm missing the mark—let's talk about it.
Cheers!
Robb

