Building Toward Amsterdam: Why I'm Making the Bull Case for Cisco's Transformation
I'm building the bull case for Cisco's transformation. In public. With full awareness of my bias. The market treats every announcement as discrete news—but I think there's a coherent narrative nobody's connecting. Let's test if the optimism holds up.
The series kickoff: A Cisco optimist stress-testing whether the transformation story is real
Let me be direct about what this is.
I've spent most of my career at Cisco. I'm a fan. Not the blind kind—I've watched the stumbles, the acquisitions that never quite integrated, the "transformations" that turned out to be rebranding exercises. But I'm also someone who believes there's something real happening right now that deserves a better telling than it's getting.
So I'm spending the next few months building the bull case for Cisco's transformation. In public. With full awareness of my bias.
Here's why: Cisco Live Amsterdam is in February 2026, and I'll be hosting conversations there again (I've lost count of how many events at this point, going back to when they called it Networkers and wouldn't let me in). I need to show up with more than surface-level talking points. I need a coherent framework for understanding what Cisco's attempting, why it might actually work this time, and what would prove me wrong.
And here's the thing—I think the market is missing something. The analyst coverage treats every Cisco announcement as discrete news. Splunk gets the observability press. Hypershield gets security media attention. Silicon One shows up in networking outlets. But nobody's connecting them into a coherent narrative.
I think there IS a narrative. A good one. Maybe even a great one.
But I could be wrong. So I'm going to articulate the optimistic case as clearly as I can, identify what would disprove it, and invite you to pressure-test the logic.
That's the experiment.
What I'm Actually Trying to Do
This isn't neutral analysis. I'm not pretending to be an objective industry observer weighing Cisco against competitors with perfect evenhandedness.
I'm building the most defensible version of the bull case. The sophisticated optimist's argument for why Cisco's current moves might actually deliver on the integration and unification promises that previous "transformations" didn't.
Think of this as advocacy journalism with technical rigor. I'm making a case, not just reporting facts. But I'm doing it with:
- Explicit acknowledgment of bias (you're reading it right now)
- Technical depth that goes beyond marketing messaging
- Clear articulation of what would prove me wrong
- Invitation to challenge the logic
I've spent my career helping people inside and outside Cisco improve their "fan boy" skills—understanding the technology deeply enough to explain why it matters. This is that, at scale, focused on the strategic level rather than individual products.
By Amsterdam, I want to know whether I'm seeing real signal or just seeing what I want to see.
The Situation: Too Many Dots, Not Enough Lines
Here's what Cisco has done in the past 18 months:
Acquired Splunk for $28 billion—their largest acquisition ever. Launched Hypershield, calling it "the most radically different security innovation" in years. Pushed Silicon One for AI networking while everyone else debates InfiniBand versus Ethernet. Shipped AgenticOps, AI Assistants, Secure Connect, Security Cloud Control, and about seventeen other things with "AI" or "Cloud" in the name.
Any one of these could be a major story. Together? It's overwhelming.
And here's what bothers me: most coverage treats these as disconnected tactical moves. Splunk gets positioned as an expensive hedge against declining networking revenue. Hypershield gets covered as "Cisco tries security innovation again." Silicon One gets framed as "playing catch-up to Arista."
What if that's wrong? What if these are all pieces of a genuinely coherent architectural transformation?
That's the case I'm building.
My Thesis: There's a Three-Part Playbook
After digging through analyst reports, podcasts, earnings calls, and about forty blog posts, I see a pattern:
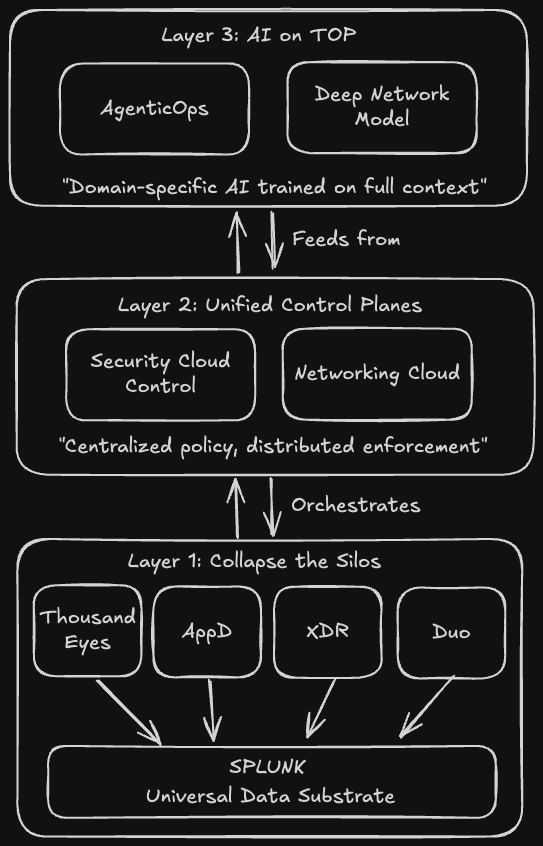
1. Collapse the silos
For years, Cisco's had best-in-class point solutions that didn't talk to each other properly. ThousandEyes saw network paths. AppDynamics saw application performance. XDR saw security events. Different data formats, different consoles, different operational models.
The Splunk acquisition is the universal data substrate that lets all these tools actually correlate their telemetry. That's the thesis, anyway.
2. Unify the control planes
Security Cloud Control becomes the single operational layer for security. Networking Cloud does the same for Catalyst, Meraki, and SD-WAN. The vision: distributed enforcement (security everywhere, networking everywhere) with centralized policy and orchestration.
3. Layer AI on top
Once you have unified data and unified control, you can build meaningful AI. Not "AI-washing" existing products, but domain-specific models trained on correlated network, security, and application telemetry. That's what AgenticOps and the Deep Network Model are supposed to be—AI that understands your infrastructure because it has the full context.
If this works—if Cisco actually pulls off collapsing these silos while maintaining the best-in-class capabilities of each component—it fundamentally changes their competitive position.
That's a big "if."
Why This Is Hard (And Why I Might Be Wrong)
Let's talk about the elephant in the room: Cisco's integration track record is mixed at best.
Meraki took years to properly integrate with the broader portfolio. AppDynamics largely remains standalone. ThousandEyes is barely connected to the rest of the stack. Different business units have operated semi-independently, with inconsistent integration approaches and management styles that don't always align.
Now Cisco is attempting to integrate:
- Their largest acquisition ever ($28B Splunk)
- With completely different culture and tech stack
- While also absorbing Isovalent for Hypershield
- And unifying control planes across networking and security
- And building AI capabilities on top
The degree of difficulty here is extraordinary.
Here's what would prove me wrong:
- Splunk remains operationally separate 18 months post-acquisition
- The "unified data substrate" turns out to be just API integrations, not deep architectural unity
- AgenticOps and AI Assistant ship but underdeliver—essentially branded wrappers around generic LLMs
- Security Cloud Control and Networking Cloud stay siloed from each other despite the naming
- Customers keep buying individual Cisco products but reject the integrated platform story
But here's why I think it might be different this time: something shifted over the last few Cisco Live events. The integration story became more credible. The technical architecture started showing real unification, not just marketing slides. Whether that momentum carries through the Splunk integration—the ultimate test—is what I'm watching for.
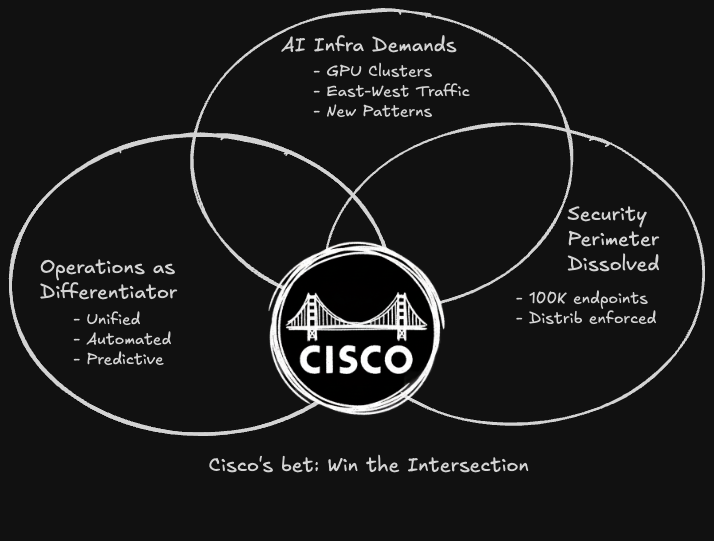
The Market Context
Three simultaneous disruptions are reshaping enterprise IT:
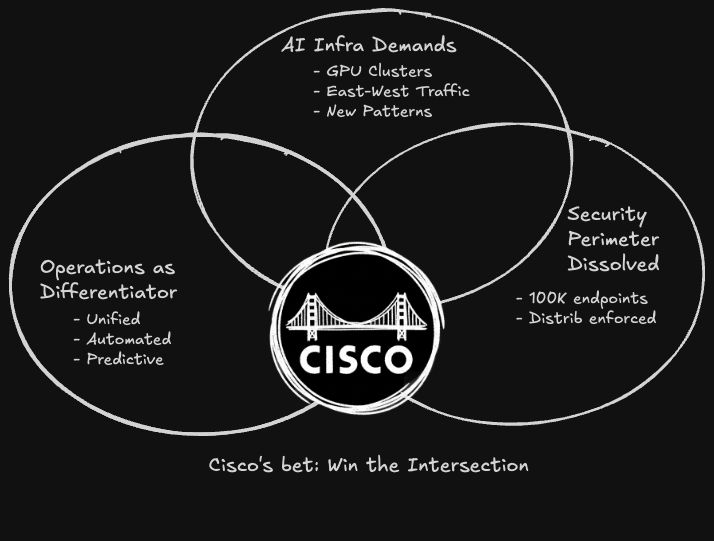
AI is creating entirely new infrastructure demands. Training clusters need networks that can handle massive east-west traffic. Inference workloads need ultra-low latency. Security models have to protect AI assets and detect AI-powered threats. A customer deploying a mid-sized GPU cluster suddenly needs 10x the network bandwidth between racks than they needed for traditional compute—with completely different traffic patterns.
The security perimeter has fully dissolved. Not "is dissolving"—it's done. Hybrid work, multi-cloud, edge computing, IoT—it's all reality now. The new challenge isn't accepting the perimeter is gone; it's operationalizing security at a scale where you have hundreds of thousands of enforcement points instead of dozens of appliances.
Operations has become the differentiator. Raw performance? Everyone can build faster silicon. More features? Software eats everything, so feature parity arrives quickly. But operational simplicity—unified visibility, automated remediation, predictive intelligence—that's hard to replicate. When a network incident happens at 2 AM, the team that can identify root cause in minutes versus hours isn't just more efficient—they're operating in a different league.
Cisco's transformation directly addresses all three shifts. If they execute, they're positioned for the next decade. If they stumble, they risk becoming infrastructure of the past.
Now, are they leading these trends or playing catch-up? Honest answer: mixed. Arista is ahead in AI networking mindshare. Palo Alto is further along in SASE execution. Datadog has more modern observability positioning.
But here's the optimistic case: Cisco doesn't need to be first. They need to be integrated and operationally simpler. If they can deliver on the unified data + unified control + meaningful AI stack, they're offering something competitors can't easily replicate.
That's the bet.
The Plan: Eight Deep Dives
Over the coming weeks, I'm diving into these areas:
Silicon One & AI Networking - Why Cisco's Ethernet bet for AI infrastructure might be smarter than the InfiniBand hype suggests. It's about operational familiarity and optionality, not just raw performance.
Hypershield - How distributed security using eBPF represents a genuine architectural shift. The Isovalent acquisition makes this credible—if the integration actually happens.
Splunk Integration - Why this $28B acquisition is either the connective tissue that makes everything work, or an expensive mistake that proves integration skeptics right. This is the test case.
AgenticOps & AI Assistant - What it would take for domain-specific LLMs trained on network and security telemetry to be real versus vaporware. Here's what I'm watching for.
Secure Connect & SASE Evolution - How Cisco's SASE story matured from "our way or the highway" to "we'll meet you where you are." Pragmatism might be strategy.
Security Cloud & Identity - The control plane unification story, and whether Duo + Identity Intelligence actually delivers continuous identity security at scale.
Networking Cloud - Whether Meraki and Catalyst sharing a common operational model is real or just better marketing. Years in the making; is it actually shipping?
The Synthesis - How all these pieces connect, what's still missing, and what to watch for in Amsterdam. The complete bull case, stress-tested.
Each piece will be technical enough to be useful, accessible enough to share with non-engineers. The goal is building the strongest possible version of the optimistic case—then seeing if it holds up.
What I Don't Have
Let me be clear about limitations:
I don't have inside information. Even when I was at Cisco, I never had unique access to strategy discussions. Everything here comes from public sources—analyst coverage, technical docs, customer case studies, earnings transcripts.
I'm not a Cisco employee, so I don't know the internal debates, the budget fights, the technical debt, or which executives are driving decisions versus taking credit.
I'm hosting their Amsterdam event, which creates both access and bias. I'll get to ask questions others won't, but I also have professional incentive to find a good story.
And most importantly: The integration might not happen. The AI might underwhelm. Customers might reject the unified platform and keep cherry-picking products. The through-line I'm seeing might be narrative construction rather than strategic reality.
That's why I'm articulating this as a bull case rather than a prediction. I think there's something real here. I want it to be real. But I'm testing that belief, not asserting it as fact.
Why Amsterdam Matters
Cisco Live is where strategy meets reality.
The keynotes show how Cisco's positioning these moves for 2026. The breakout sessions reveal what's actually shipping versus still on roadmap. Customer panels show whether the integration story resonates or gets met with skepticism. Partner conversations indicate whether the ecosystem is bought in or hedging bets.
And the hallway conversations—the questions that don't get asked in recorded sessions, the things people say off the record—that's where you learn what's working and what's not.
I want to show up prepared. With a clear framework for the optimistic case, specific predictions about what success looks like, and honest articulation of what would prove me wrong.
By February 2026, I want to know whether Cisco's transformation is real or whether I've been constructing a narrative I wanted to see.
The Invitation
Here's the deal: I'm building the bull case. But I don't want it to be a weak bull case based on wishful thinking.
If you're a customer deploying this stuff, tell me where reality diverges from the integration story. If you're a partner, share where the friction points are. If you're an engineer, explain which architectural decisions seem sound versus questionable. If you're a competitor or skeptic, show me where the logic breaks down.
I'll publish my thinking as it develops. You can strengthen it, challenge it, or tear it apart. By Amsterdam, we'll know whether the optimistic case holds up.
And if you're planning to be in Amsterdam or watching remotely, this series will give us shared language for those conversations. You'll know what I'm looking for. I'll know what questions you care about. We can skip the setup and get to substance.
I'm making the bull case. Help me make it bulletproof—or show me why it can't be.
Up next: Silicon One and why Cisco's Ethernet bet for AI networking deserves more credit than it's getting. We'll dig into the technical architecture, the operational advantages, and why being second-to-market might actually be the smarter play.
Your take? What am I missing? Where does the optimistic case break down? What should change my mind? Let me know—this only works if you pressure-test the logic.
This is post one of an eight-part series building toward Cisco Live Amsterdam 2026. I'm making the bull case for Cisco's transformation and testing whether it holds up. Follow along to see if the optimism is justified.

