When Cloud Security Meets Geopolitical Reality: A Framework for Digital Sovereignty
When cloud security meets geopolitical reality, even the most sophisticated systems can be undermined by legal and jurisdictional pressure points. Learn how the Trust Descent Triangle maps your real vulnerability and the Sovereignty Ascension Pyramid charts your path to digital control.

Picture this: It's 2 AM, and you're getting calls that your organization's "secure" cloud communications system might be cut off in 72 hours. Not because of a cyberattack or technical failure, but because of escalating tensions between your country and the nation where your cloud provider operates.
This scenario isn't hypothetical. It's happening worldwide, forcing us to rethink what "secure" really means in our interconnected world.
Over recent months, I've been working with organizations grappling with this challenge. What I've discovered is that understanding where you actually stand on the security spectrum is the first step toward making informed decisions about your most critical systems.
I started by developing what I call the Trust Descent Triangle - a framework for mapping your real vulnerability.
Why I Created This Framework
As someone who's spent years helping organizations verbalize and contextualize their technology challenges, I kept seeing the same pattern. Companies would invest heavily in what they believed were secure, sovereign solutions, only to discover that their control was more illusion than reality.
The sovereignty angle is relatively new—emerging as both a logical correction to the over-emphasis on "cloud for everything" and a response to dramatic shifts in global alliances and an erosion of trust in a world of exploding AI capabilities.
The wake-up call usually came in one of two ways: either through a crisis that exposed their dependencies, or through growing awareness that their most critical communications were ultimately governed by foreign legal systems and political decisions. Microsoft's recent revelations about European sovereign cloud control illustrate this challenge perfectly.
What became clear is that we needed a way to map where organizations actually sit on the security spectrum - not where they think they are, but where they really are. As simple as this may appear, it's a framework for understanding your position, not an instruction list for what to do about it.
The Trust Descent Triangle: Mapping Your Vulnerability
This is how the Trust Descent Triangle came to be—and yes, the counterintuitive name is intentional.
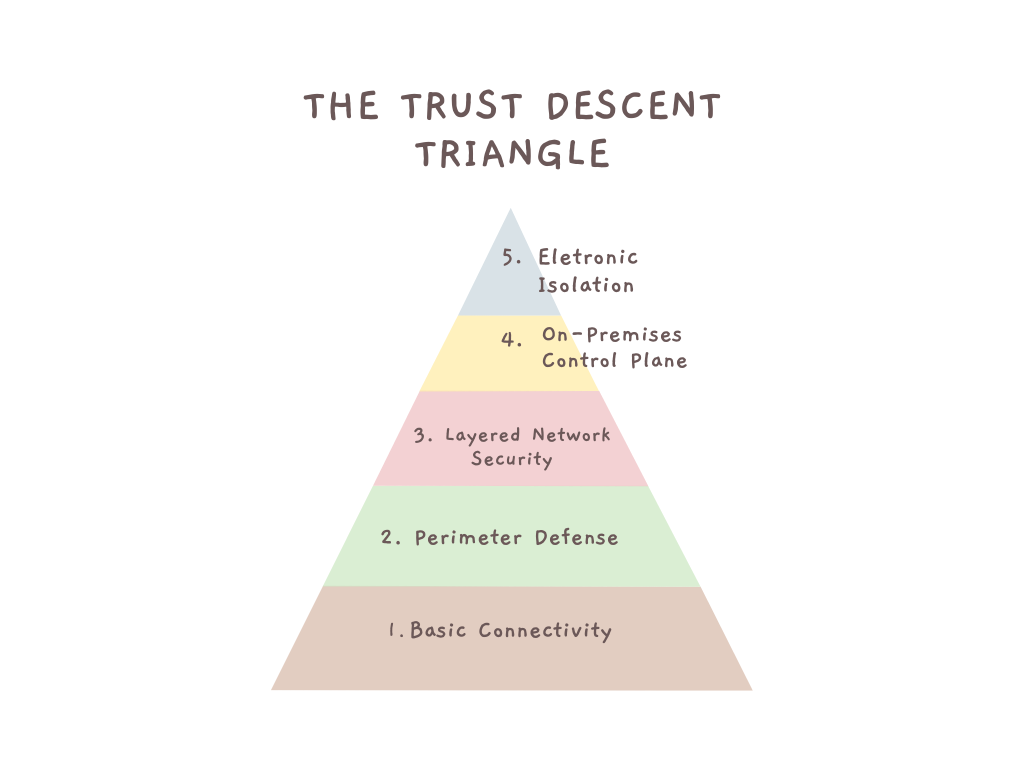
As you move down this pyramid, your trust in external systems plummets, but your actual security soars. It reveals five distinct levels of security posture, from basic connectivity all the way to complete electronic isolation.
Most organizations today hover around level three—and for many applications, that's perfectly appropriate. But the framework helps you think through which systems truly need higher levels of control. When evaluating your crisis management communications or board meetings discussing sensitive decisions, the key question becomes: what happens if this system becomes unavailable or compromised due to forces beyond our control?
The Sovereignty Ascension Pyramid: Your Path Forward
But mapping vulnerability is only half the story. I didn't want to leave organizations feeling hopeless about their situation. Understanding where you stand is valuable, but knowing how to move forward is essential.
That's why the Sovereignty Ascension Pyramid came to be - not to replace the Trust Descent Triangle, but to complete it. It takes the same control points we identified and shows how to systematically reclaim them.
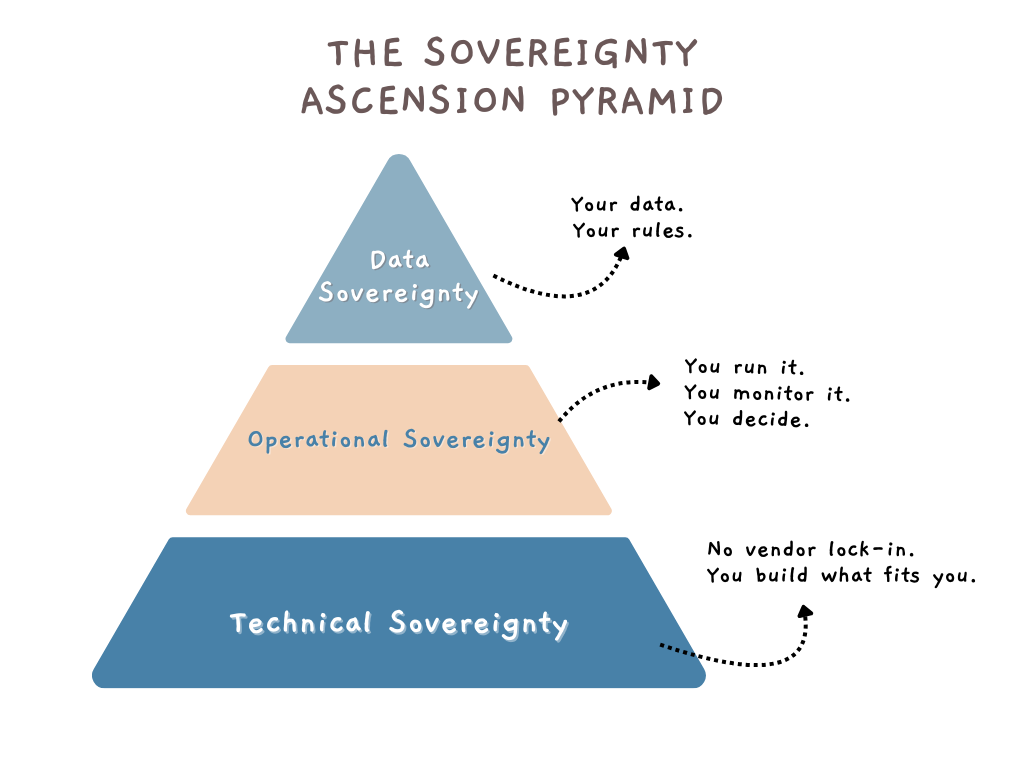
This framework is built on three critical pillars:
- Technical Sovereignty: You choose the tools, avoid lock-in, and design your architecture to suit your needs, not theirs.
- Operational Sovereignty: You control the operations—updates, workflows, and visibility into every action.
- Data Sovereignty: Your data stays in your jurisdiction, but more importantly, you decide who can access it, when, and how.
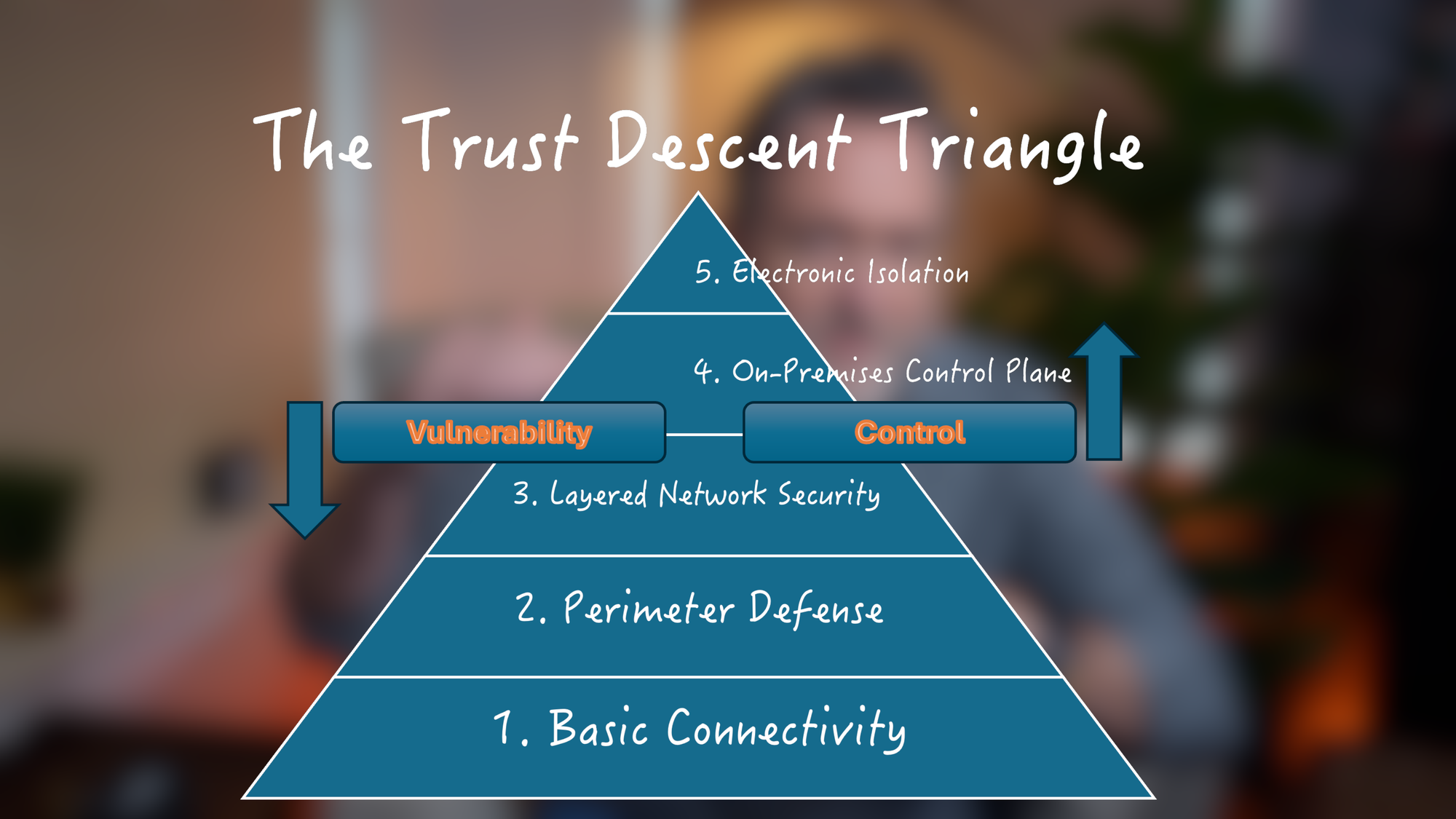
The critical transition from level three to level four marks the boundary between vulnerability and control. It's also where possibility begins—where you move from appreciating the cloud's convenience to demanding control that no remote provider can revoke.
Why This Matters Now
The acceleration around these issues has been dramatic. Geopolitical tensions are forcing organizations to confront uncomfortable questions about their digital dependencies. Even the most sophisticated cloud security systems can be undermined—not necessarily by technical flaws, but by legal and jurisdictional pressure points.
Cloud providers understand these concerns, which is why many are developing sovereign cloud offerings. These represent thoughtful responses to a complex landscape of risks. But there's an important nuance that often gets overlooked: while your data might physically reside within your borders, the control systems—the mechanisms that govern access, policy, and operations—may still be managed from the provider's home country.
The Practical Path Forward
The organizations that thrive in this environment will be those who proactively secure their most critical communications, not those who react once compromise has already occurred.
Let me be clear: this isn't about abandoning cloud services entirely. Cloud and SaaS services aren't going away, nor should they. I think of this more as a "buyer beware" situation. The world is changing, and so are the various weights we assign to both new and old threat vectors.
This is about making strategic choices about which systems require true sovereignty. Not every system needs level five security, but for those that do, you need partners who've been solving sovereignty challenges long before it became a buzzword.
Companies like VQ Communications have been addressing exactly this challenge since 2006, helping organizations build truly sovereign video infrastructure that operates entirely within their control, with no external dependencies. What's particularly compelling about their approach is how they handle the level three to level four transition—instead of forcing you to rip out existing infrastructure, they add sovereign control layers that let you keep your investment while reclaiming your control plane.
What's Next
The question isn't whether this shift toward digital sovereignty is coming—it's whether you'll be ready when your organization needs to make the move.
Start with the Trust Descent Triangle assessment. Map your critical systems. Then use the Sovereignty Ascension framework to chart your path forward.
Because in a world growing more unpredictable by the day, digital sovereignty isn't just a nice-to-have. It's survival.
Both videos in this series dive deep into the frameworks and practical implementation strategies discussed here. Whether you're just beginning to think about digital sovereignty or you're ready to take concrete steps toward reclaiming control, these frameworks provide a roadmap for navigating the complex intersection of security, geopolitics, and business continuity.

