The Synthesis: How the Storylines Converge in Amsterdam
After months of deep dives, the picture is clear: Cisco’s architecture is real, but the hardest parts—automation, cross-domain operations, trust—are still forming. Amsterdam will determine whether this becomes the new baseline or stays a bold hypothesis.

Part of "Building Toward Amsterdam" - A public learning exercise ahead of Cisco Live EMEA 2026
TL;DR
- Cisco’s architectural choices are real, but integration is uneven.
- The foundation (Silicon One, Splunk, Deep Network Model) is strong.
- Operations automation is the execution risk.
- Amsterdam will reveal whether unified architecture is working in the wild—or still a promise.
Introduction
Here’s what I’ve been trying to figure out for the past six months:
Is Cisco’s transformation architecturally real—or just point products with better branding?
I’ve written seven deep-dives to chase that answer:
- Silicon One — The hardware foundation for AI-era networking
- Hypershield — Cisco's Bet That Security Belongs in the Data Path, Not Bolted to the Side
- Splunk — The $28 B Bet That Finally Gives Cisco a Data Operating System
- AgenticOps & AI Canvas — When AI Actually Understands Your Network
- Security Cloud Control & Identity Intelligence — When Identity Becomes the Correlation Layer
- Networking Cloud — When Meraki and Catalyst Finally Speak the Same Language
- Building Toward Amsterdam: Why I’m Making the Bull Case for Cisco’s Transformation
Each piece stands on its own. Each reflects a real strategic choice.
But if these pieces aren’t connected, it’s not transformation. It’s theater.
And that’s the question we’re running out of time to answer.
Amsterdam 2026 is two months away. This is where narrative meets reality.
Here’s what actually ties these storylines together, what’s still missing, and the signals I’m watching to judge whether Cisco’s rebuild is credible or aspirational.
Why This Matters
This isn’t just a Cisco story. It’s a story about how enterprise infrastructure is going to operate for the next decade.
If Cisco’s integrated approach works, teams get a unified operational model, cross-domain visibility, safer automation, and the ability to run AI-era infrastructure without scaling headcount at the same rate as complexity.
If it doesn’t—fragmentation wins, operational overhead keeps rising, and organizations end up stitching together even more tools, dashboards, and policy engines.
Either way, the outcome affects how architects design, how operators work, how budgets shift, and how organizations plan for the AI wave that’s already here.
The Through-Line: How These Pieces Actually Fit Together
Let's start with what's genuinely connected, because this is where the bull case gets real.
The Problem Cisco Is Solving
Enterprises face three converging challenges in the AI era:
Challenge 1: Infrastructure has to scale to AI demands. Datacenters that were built for business applications are now hosting GPU clusters running trillion-parameter models. Networks need 800G, sub-microsecond latency, and intelligent packet steering. The old architecture doesn't survive this transition.
Challenge 2: Operations can't keep up with complexity. Traditional network and security operations assume you're managing predefined domains. But AI workloads are distributed, dynamic, and demand real-time optimization. Manual operations don't scale. You need AI-assisted automation to keep up.
Challenge 3: Security can't be added afterward. When AI is embedded in your infrastructure, when workloads move at machine speed, when traffic flows east-west across your data center, perimeter security doesn't work. Security has to be integrated into the operational fabric from the start.
Cisco's transformation addresses all three simultaneously. Which is rare. Most vendors pick one problem and optimize for it.
How the Stack Actually Works
Layer 1: Hardware optimized for AI workloads (Silicon One, Catalyst 9300/9400, Nexus HyperFabric)
Silicon One ASICs provide the performance, telemetry, and programmability for AI-era networking. Intelligent Packet Flow (Cisco's adaptive routing) steers traffic based on real-time congestion. Nexus HyperFabric AI provides the fabric architecture for data center AI clusters.
This generates rich telemetry about network behavior at hardware speed.
Layer 2: Distributed security enforcement embedded in the data path (Hypershield)
Hypershield uses eBPF technology (from the Isovalent acquisition) to embed security agents directly into the data path. Not as a bolt-on appliance, but as a distributed fabric running on smart switches, DPUs, and endpoints.
This generates security telemetry from enforcement points across your infrastructure.
Layer 3: Unified data substrate (Splunk)
Both network and security telemetry flow into Splunk as a normalized, indexed data fabric. Different sources, different formats, unified schema. This is what enables cross-domain reasoning.
Without Splunk, network events and security events are separate signals. With Splunk, they're one story.
Layer 4: Domain-specific AI trained on unified data (Deep Network Model)
Cisco trained the Deep Network Model—a large language model specifically on network and security data from their customers. Not generic AI that happens to know about networking. Domain-specific AI that understands the relationships between network topology, traffic patterns, security policies, and application performance.
This model is embedded in AgenticOps and powers the AI Assistant across all Cisco platforms.
Layer 5: Unified operational platforms (Networking Cloud, Security Cloud Control)
Networking Cloud and Security Cloud Control converge Meraki and Catalyst on a single operational model. Networking and security policies are defined once and enforced consistently across environments. Identity-based access control is native to the platform.
Layer 6: Agentic automation across domains (AI Canvas, AgenticOps, Workflows)
Rather than separate tools for networking, security, and observability, Cisco AI Assistant and AI Canvas orchestrate workflows that reason across all domains. Detect a security event → correlate network data → recommend remediation → execute safely → learn and optimize.
Each layer depends on the ones below it. Remove Splunk, and the Deep Network Model has no training data. Remove unified platforms, and automation can't orchestrate consistently. Remove distributed security, and you still have perimeter-based vulnerabilities.
But together, they form something genuinely different: infrastructure that understands itself, secures itself, and optimizes itself.
Where This Competes
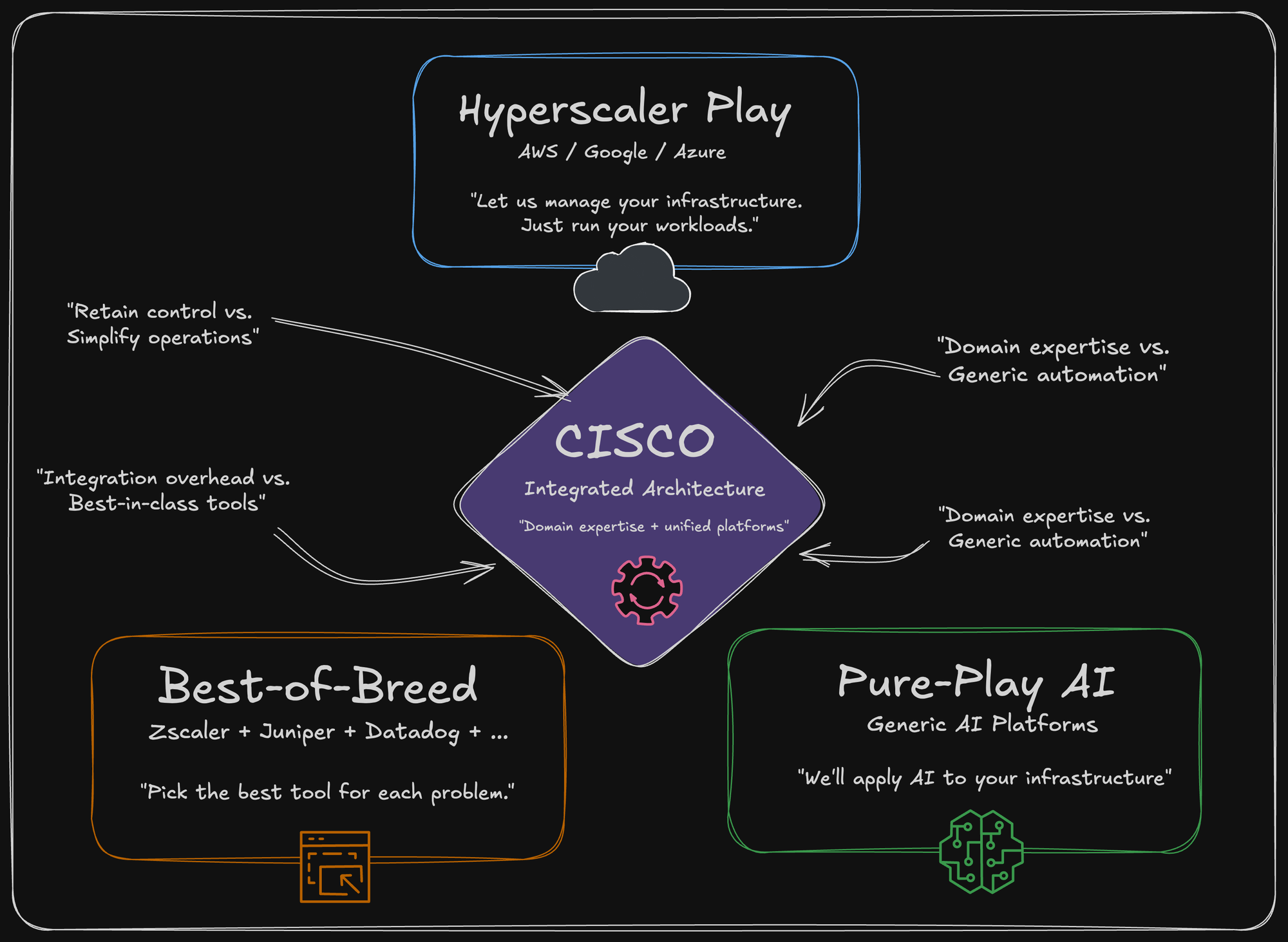
This architecture competes against three different approaches:
The hyperscaler play (AWS/Google/Azure): "Let us manage your infrastructure. You just run your workloads."
Cisco's counter: "You need to understand and control your infrastructure. We give you the tools to do it intelligently."
The best-of-breed fragmentation (Zscaler + Juniper + Datadog + X): "Pick the best tool for each problem."
Cisco's counter: "Integration complexity kills simplicity and automation. Unified platforms move faster."
The pure-play AI startup approach (Datadog, ServiceNow, etc): "We'll apply generic AI to your infrastructure."
Cisco's counter: "Generic AI doesn't understand network causality. Domain-specific AI trained on network data is 20% more accurate and actually solves real problems."
Each of these is a credible competitive position. Cisco's position is that integrated infrastructure with domain expertise beats specialized point solutions or generic AI.
That's testable. And we'll know in Amsterdam whether they're right.
What's Actually Shipping vs. Still Roadmap
This is the credibility test.
| Component | Status | Shipping | Evidence |
|---|---|---|---|
| Hardware (Silicon One, Catalyst 9300/9400) | Production | Yes | Q3 2025+ deployments confirmed |
| Hypershield enforcement | Production | Partial | Monitoring agents shipping; execution agents still limited preview |
| Splunk unified data fabric | Production | Yes | Available now, integrations deepening |
| Deep Network Model | Production | Yes | Embedded in AI Assistant, 20%+ accuracy improvement demonstrated |
| Networking Cloud (Global Overview) | Beta → GA | Q4 2025 | Beta starting this month |
| Cloud-managed fabric | Beta → GA | Q1 2026 | Beta Q4 2025, GA Q1 2026 |
| Security Cloud Control | Production | Yes | Available now, MSP capabilities added Nov 2025 |
| Unified identity (Access Manager) | Production | GA Q4 2025 | Available now in pilot |
| AgenticOps execution agents | Limited preview | 2026+ | Still trust-building phase |
| AI Canvas full cross-domain reasoning | Limited preview | 2026+ | Being tested with select customers |
| End-to-end autonomous remediation | Roadmap | Unknown | Not yet proven at scale |
The pattern: foundation is solid. Operations automation is where execution risk sits.
The Honest Assessment: Where Integration Is Real vs. Still Aspirational
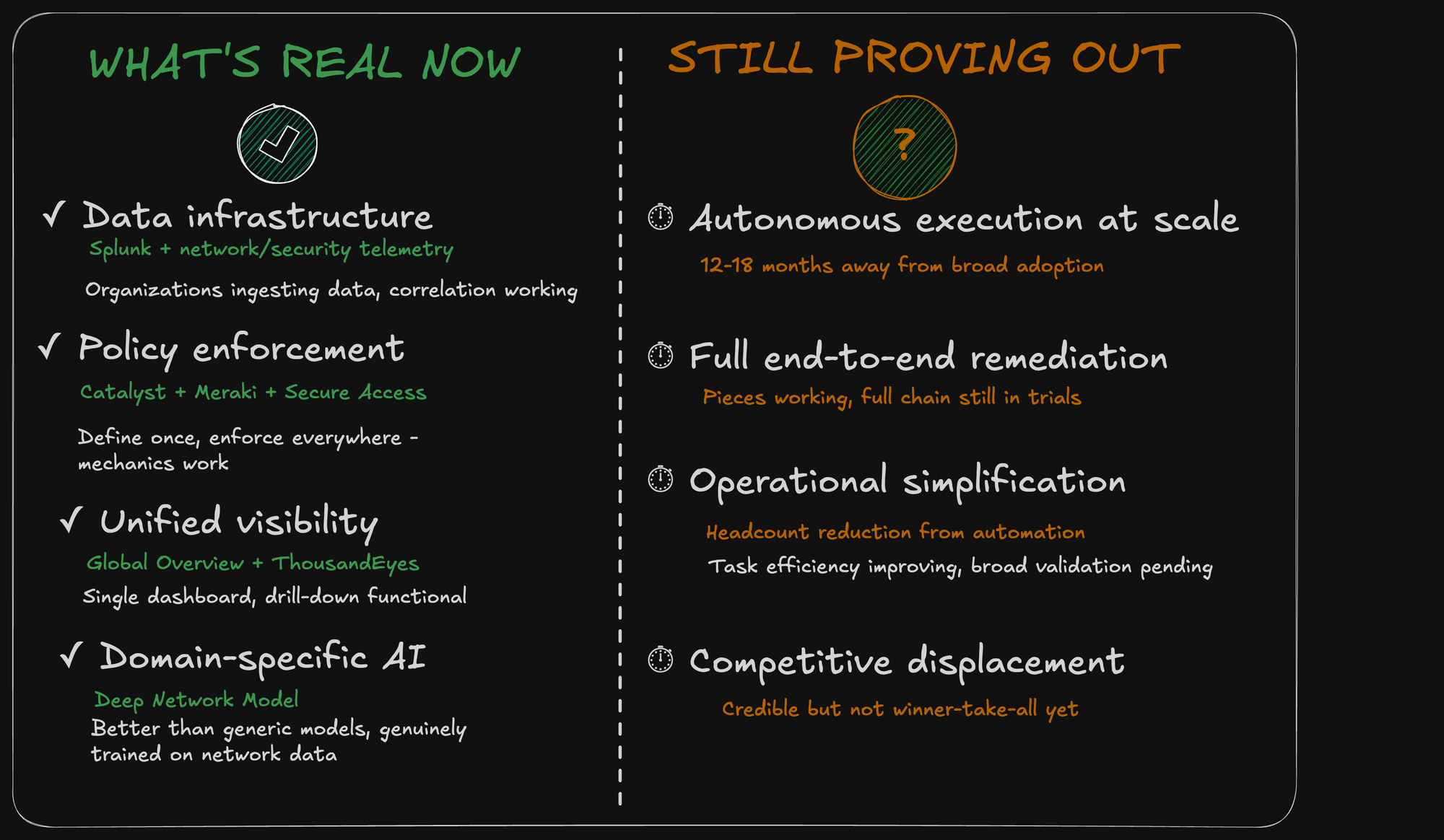
What's Genuinely Integrated
1. Data infrastructure (Splunk + network/security telemetry): This is real. Organizations are ingesting Catalyst, Meraki, ThousandEyes, XDR, and application data into Splunk. The correlation is working. Analysts are seeing cross-domain insights they couldn't see before.
2. Policy enforcement (Catalyst + Meraki + Secure Access): This is real. You can define identity-based policies once and have them enforced consistently across campus, branch, and cloud. The mechanics work.
3. Unified visibility (Global Overview + ThousandEyes): This is real. You can see your entire network—cloud and on-prem—in one dashboard. Drill down works. Correlation across layers is functional.
4. Domain-specific AI (Deep Network Model): This is real. It's producing better insights than generic models. It's genuinely trained on network data, not just fine-tuned from a generic foundation.
What's Still Aspirational
1. Autonomous execution at scale: The concept works. The trust mechanisms are being built. But broad enterprise adoption of "AI executes network changes autonomously" is still 12-18 months away.
2. Full end-to-end remediation: "Detect issue → diagnose root cause across domains → remediate → validate" in one automated loop is the vision. Pieces are working. The full chain is still in controlled trials.
3. Operations simplification translating to headcount reduction: We know task-based efficiency is improving (less time on routine work). Whether this actually means IT teams can be smaller is still being proven. Early evidence is good; broad validation is pending.
4. Competitive displacement of alternative approaches: Cisco is credible for integrated infrastructure. But hyperscalers are still easier for workload portability. Best-of-breed still wins in specific domains. This isn't a "winner take all" dynamic yet.
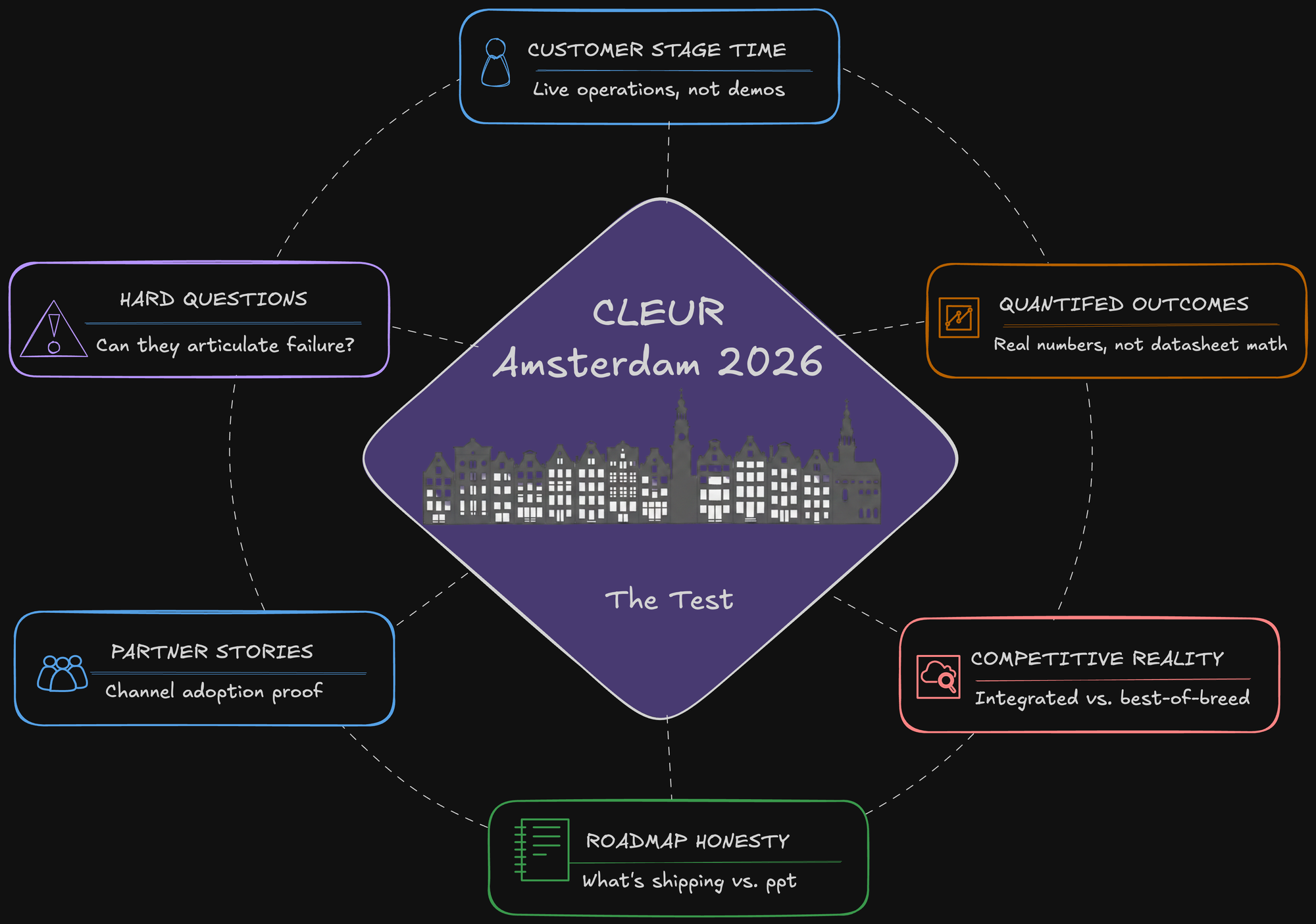
What I'm Actually Watching For in Amsterdam
Here are the specific signals that will tell me whether this is real or aspirational.
1. Customer Stage Time with Live Operations
I want to see customers on stage demonstrating this stack in live operations. Not simulations. Not pre-recorded demos. Real infrastructure, real data, real complexity.
The test:
- A customer managing 100+ sites across cloud and on-prem
- An actual operational scenario (not a contrived demo scenario)
- Global Overview showing unified visibility
- An issue identified, correlated across domains, and remediation proposed
- Full transparency about edge cases and limitations
If Cisco can show this smoothly, it's real.
If demos are polished but fragile, or if they pivot to pre-recorded segments when something goes wrong, that tells a story.
2. Quantified Business Outcomes
"Faster deployment," "reduced operational overhead," "lower mean-time-to-resolve" are marketing language.
What I want to hear:
- Specific numbers from real customers
- Before/after timelines for actual changes
- Headcount impact (if any) from automation
- ROI calculations from actual pilots
Not Cisco-sponsored case studies. Actual customer willingness to put their reputation on the outcome.
3. Competitive Differentiation vs. Reality
Cisco will claim their integrated approach beats alternatives. I want to see how they actually differentiate when tested.
The scenario:
- Customer running Catalyst on-prem + AWS cloud workloads
- Customer using Zscaler for SASE + Datadog for observability + Arista for cloud networking
- Cisco's unified approach vs. the fragmented approach
- Which one actually delivers the promised simplicity?
This is where I'll learn whether integration is real or marketing.
4. Honesty About What's Still Roadmap
The strongest signal of credibility is when Cisco executives clearly separate what's shipping from what's still being built.
How I'll judge:
- Do they acknowledge roadmap items vs. GA products?
- Do they admit where competitors have advantages?
- Do they discuss tradeoffs honestly?
- Do they acknowledge implementation complexity?
If the entire narrative is "we've solved everything," that's a red flag. If there's nuance and honesty about what's proven and what's emerging, that builds credibility.
5. Partner Ecosystem Stories
Cisco's strategy depends on partners implementing this stack successfully. Channel stories are the proof of actual adoption.
What I'll listen for:
- Ease or difficulty of partner implementation
- Real customer feedback from partner interactions
- Margin impact for partners
- Competitive pressure from alternative ecosystems
Partner satisfaction is lagging indicator of real-world viability.
6. The Hard Question: What Would Prove You Wrong?
The best test of credibility: Can Cisco articulate what would prove their thesis wrong?
- "If AgenticOps can't achieve >90% accuracy on autonomous remediation, we haven't solved it."
- "If Networking Cloud adoption plateaus after the early adopters, we misunderstood operational complexity."
- "If cloud-managed fabric doesn't simplify campus deployments, we overbuilt abstraction."
If Cisco can articulate failure conditions, they're thinking clearly about risk.
If they only have positive narratives, they're selling.
The Inflection Point
Amsterdam isn’t just an industry conference—it’s a referendum on whether unified architecture can actually beat the gravitational pull of complexity. Every vendor promises simplification; very few deliver it. Cisco is betting that data, intelligence, and operations can finally converge into a coherent system. The question now is whether that convergence shows up in customer outcomes, not just product strategy slides. That’s the moment we’re walking into.
A Quick Note on My Own Bias
I want the integrated approach to work. Fragmented operations are crushing teams, and a unified model—if it actually delivers—would make infrastructure meaningfully simpler. But wanting it to be true isn’t the same as believing it blindly, which is why I’m watching Amsterdam for proof, not promises.
The Bull Case vs. The Reality Check
Here's both sides:
The Bull Case (Why This Transformation Matters)
If Cisco executes well, this represents a genuine architectural shift in enterprise infrastructure:
Today's fragmentation: Separate teams for network/security/observability. Manual correlation. Point solutions optimized individually. Operations as bottleneck.
Cisco's integrated approach: Unified operational model. Automatic cross-domain correlation. Built-in intelligence. Teams handling 10x scale with same headcount.
The impact compounds. Early adopters get easier deployments, faster troubleshooting, better security. That creates competitive advantage, drives adoption, builds a moat.
If this is how infrastructure works in 2027, Cisco owns the next decade.
The Reality Check (Why This Could Disappoint)
But execution risk is real, and I see specific vulnerabilities:
1. Integration complexity exceeds marketing: Unifying Meraki and Catalyst is harder than it looks. Unified policy enforcement across heterogeneous environments is brittle. Edge cases accumulate. Customers end up frustrated by complexity they didn't expect.
2. AI capabilities underwhelm: Domain-specific training is smart, but AI-driven operations still struggle with novel scenarios. Customers end up disabling automation because they don't trust it. The productivity gains don't materialize.
3. Operational adoption is slower than expected: Even if the technology works, changing how teams operate is slow. Dual-running (old + new approaches in parallel) extends timelines. ROI payback extends beyond customer patience.
4. Hyperscalers move faster: AWS, Azure, Google keep innovating. Their "managed infrastructure" story becomes increasingly compelling. Customers get tired of managing their own intelligence layer.
5. Best-of-breed wins in specific domains: Zscaler remains better for SASE in certain scenarios. Datadog remains better for observability in SaaS-first environments. Juniper remains better for service provider networks. Cisco's integrated approach doesn't win everywhere.
All of these are realistic vulnerabilities. Whether they materialize depends on execution.
My Predictions for Amsterdam
What I expect: Heavy AgenticOps emphasis. Customer stories about deployment speed and reduced overhead. Live unified visibility demos. New 2026 capabilities announced. Deepening Splunk integration. Partners discussing new opportunities. "Simplicity" as the differentiator.
What would signal credibility: Quantified customer outcomes with specific numbers. Honest separation of roadmap vs. shipping. Competitive analysis of integrated vs. best-of-breed. Discussion of where Cisco isn't winning.
What would surprise me: Major new acquisition. Deeper hyperscaler collaboration revealed. Acknowledgment of specific competitive threats. Roadmap changes from customer feedback. Pricing adjustments.
The Bottom Line
Here’s my take heading into Amsterdam:
The foundation is real. The integration is partially real. The transformation is underway but not yet proven at scale. The risk is overhyped automation. The opportunity is genuine. And the next two months will tell us whether Cisco’s architectural bets translate into operational simplicity—or remain ambitious, credible, but still aspirational.
What I'll Be Listening For in Amsterdam
Keynotes: How explicitly they describe the integration (unified data → unified intelligence → unified operations). Whether they acknowledge competitive realities. What specific metrics they cite. How they separate roadmap from GA.
Breakout sessions: "Powering the AI-Ready Data Center." "AI Changes Everything: A Blueprint for Network Security, Zero Trust, and the SOC." Deep dives on Networking Cloud, Security Cloud Control, AgenticOps. Technical depth, not marketing language.
Hallway conversations: What's working in production. Where customers hit unexpected complexity. Whether automation delivers promised efficiency. What they'd do differently if restarting.
Partner discussions: Deployment difficulty. Customer adoption patterns. Where integration breaks down. Margin impact.
Executive questions: "What would prove this approach isn't working?" "Where are you losing to competitors, and why?" "What surprised you about real-world complexity?" "What's taking longer than expected?"
The questions matter more than the answers. If Cisco executives can handle hard questions, that builds credibility.
Final Thought: Why This Matters
Cisco isn't the only company trying to simplify enterprise infrastructure. But they're unique in trying to do it through integrated architecture rather than better UI or more APIs.
If they succeed, it means unified infrastructure becomes the competitive baseline, domain-specific AI moves from experimental to operational, and operational automation becomes safe enough for broad adoption.
If they fail, it means fragmentation persists despite integration efforts, and customers prefer best-of-breed even with integration overhead.
Either outcome tells us something important about how enterprise IT will evolve.
So this isn't just about Cisco. It's about whether the next wave of infrastructure actually gets simpler or just gets more complex with better dashboards.
Amsterdam will show us which.
January is going to be crazy busy, so I wanted to wrap the series here. There may be a few out-of-band updates prior to Cisco Live if warranted. Thanks for reading along.
About the Series
Over seven deep-dives, I've analyzed:
- Silicon One — The hardware foundation for AI-era networking
- Hypershield — Security embedded in the data path
- Splunk — The unified data substrate
- AgenticOps & AI Canvas — Domain-specific AI and autonomous agents
- Security Cloud & Identity — Continuous identity security at operational scale
- Networking Cloud — Meraki and Catalyst finally speaking the same language
- This synthesis — How it all connects (or doesn't)
Each piece examines a real strategic choice Cisco is making. Whether those choices form a coherent transformation is what we're about to learn.
Series Navigation
Read the entire "Building Toward Amsterdam" series:
- Why I'm Making the Bull Case for Cisco's Transformation
- Silicon One: Why Cisco's Ethernet Bet Might Be the Smartest Play Nobody's Talking About
- Hypershield: Cisco's Bet That Security Belongs in the Data Path, Not Bolted to the Side
- Splunk: The $28 Billion Bet That Finally Gives Cisco a Data Operating System
- AgenticOps & AI Canvas: When AI Actually Understands Your Network
- Security Cloud Control & Identity: When Your Identity System Finally Sees What Your Network Sees
- Networking Cloud: When Meraki and Catalyst Finally Speak the Same Language
About this series: I'm building toward Cisco Live Amsterdam in February 2026 by making sense of Cisco's biggest strategic moves. This is part learning exercise, part knowledge sharing. I'll be hosting the Cisco Live broadcast again this year, and I want to show up with a clear understanding of the storylines Cisco's building. If something here resonates—or if you think I'm missing the mark—let's talk about it.
I'll see you in Amsterdam. And I'll be watching closely.
Sources and References:
Cisco Official Resources:
- Cisco Live San Diego 2025: Keynote Coverage
- Reinventing Infrastructure for the Next Wave of AI
- Building Critical Infrastructure for the AI Era
- Cisco Supercharges Secure Enterprise Network Architecture (November 2025)
Recent Analyst Coverage:
- NAND Research: Cisco Partner Summit Infrastructure Announcements (November 2025)
- Forrester: Key Takeaways From Cisco Live 2025
Cisco Live Amsterdam 2026:
- Cisco Live Amsterdam Official Site
- Sessions, keynotes, and thought leadership programming

