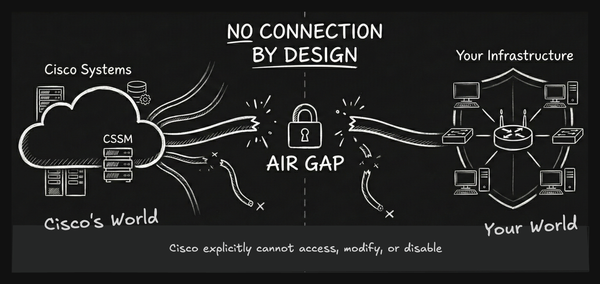
When cloud security meets geopolitical reality, even the most sophisticated systems can be undermined by legal and jurisdictional pressure points. Learn how the Trust Descent Triangle maps your real vulnerability and the Sovereignty Ascension Pyramid charts your path to digital control.