Security Cloud Control & Identity Intelligence: When Identity Becomes the Correlation Layer
Most companies think they've solved identity security with MFA and SSO. They've only solved authentication. Real identity security happens when who you are, what you're doing, and where you're doing it from get correlated in real-time across every domain—not just at login.
Part of "Building Toward Amsterdam" - A public learning exercise ahead of Cisco Live EMEA 2026
Most companies think they've solved identity security when they deploy MFA and SSO. They haven't. They've solved authentication—which is the easy part.
Identity security isn't about proving you are who you say you are at login. It's about understanding whether who you are plus what you're doing plus where you're doing it from adds up to acceptable risk—continuously, across every interaction, not just at the front door.
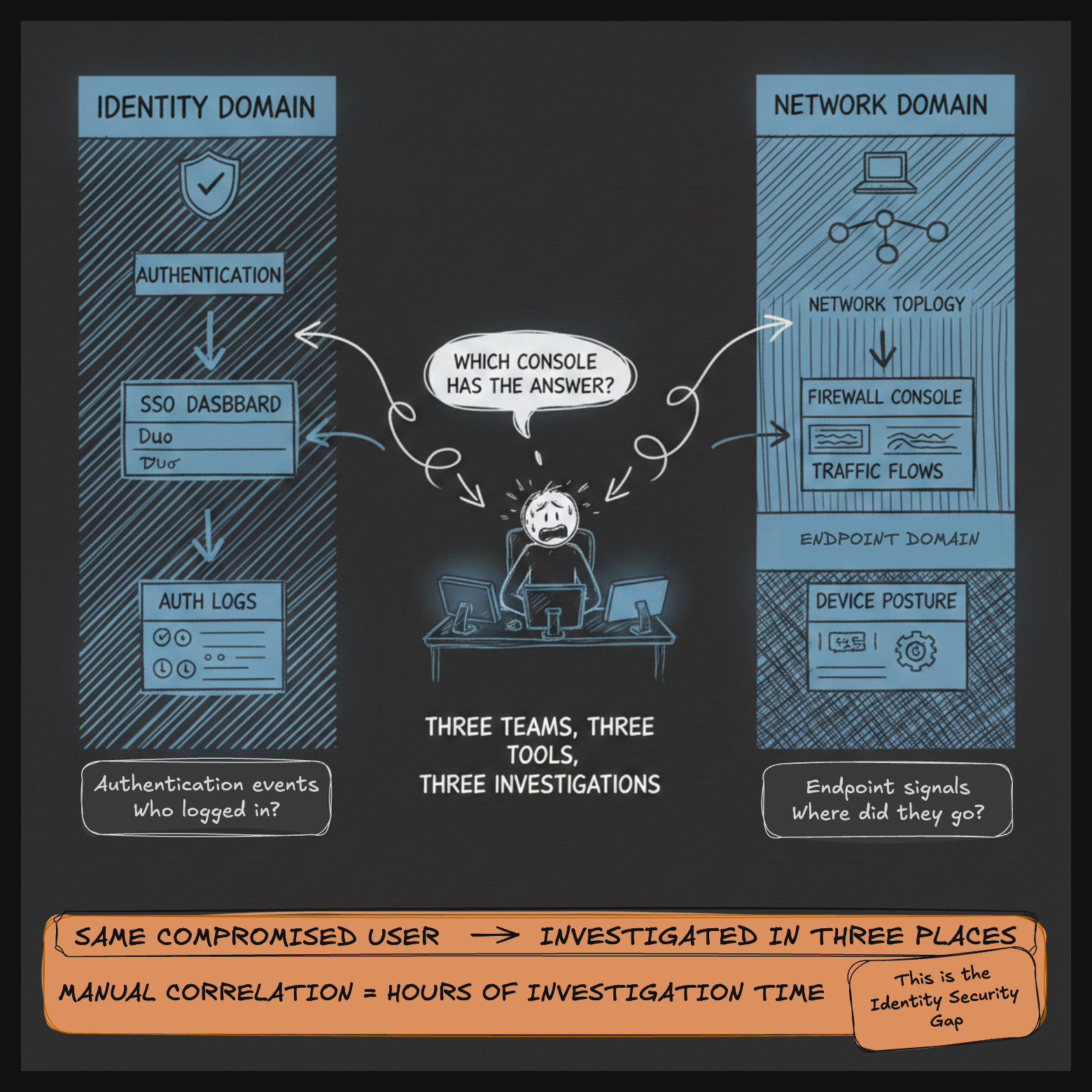
Here's the gap: your identity team sees authentication events. Your network team sees traffic patterns. Your endpoint team sees device posture. They're all looking at the same user, but none of them see the whole picture. When something goes sideways—compromised credentials, unusual user behavior, infected endpoint—you're stitching together evidence from three different consoles, three different data models, three different teams who don't naturally talk to each other.
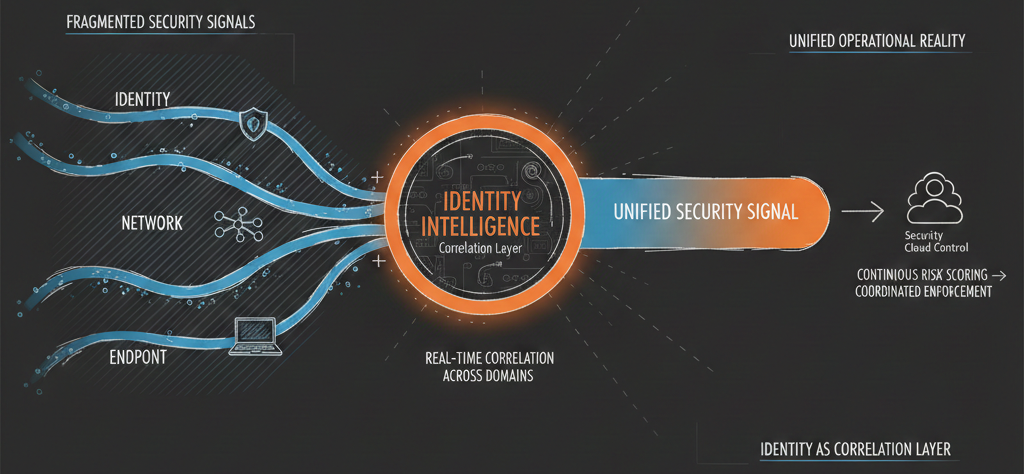
Cisco's bet is that identity becomes security only when it's correlated with everything else in real-time. Not identity plus network security. Not identity and endpoint protection. Identity as the common thread tying network telemetry, endpoint posture, and behavioral analytics into a single continuous risk signal.
This is what Security Cloud Control and Identity Intelligence are actually trying to do: collapse the operational gap between authentication, network visibility, and endpoint context so "identity security" stops being a silo and starts being the correlation layer for everything else.
The question isn't whether Cisco has the pieces—they do. Duo for identity, Splunk for correlation, Security Cloud Control for orchestration, Hypershield for enforcement. The question is whether those pieces actually talk to each other in production, or if this is still mostly architecture diagrams and roadmap aspirations.
The Problem: Identity as a Silo Inside Other Silos
Traditional identity security operates in its own world. You deploy an IdP (Okta, Entra, Duo), configure MFA policies, maybe add adaptive authentication based on geolocation or device trust. User authenticates successfully, gets a token. Fails, doesn't. Identity's job done.
But authentication is just the beginning, not the end. What happens after the user gets their token? What if credentials were compromised but the attacker authenticates from a device that passes trust checks? What if user behavior changes subtly—accessing unusual systems, from unfamiliar network segments, with degrading endpoint posture?
Your identity system doesn't see that. It authenticated once and moved on.
Your network security tools see unusual traffic patterns but don't correlate back to identity risk scores. Endpoint protection sees posture drift but doesn't feed back into identity-based access decisions real-time. Your SIEM can correlate all of this—if you've built the queries, tuned the data models, and have analysts who know how to manually stitch together identity logs, network telemetry, and endpoint signals.
This isn't just technical—it's organizational. Identity teams, network teams, and SecOps don't naturally share consoles, workflows, or success metrics. Identity measures authentication success rates. Network tracks traffic anomalies. SecOps measures mean-time-to-detect. They're all looking at security through completely different lenses.
The result: when something goes wrong, you're investigating three directions at once. Authentication logs in your IdP, network flows in your firewall, endpoint alerts in your EDR—trying to correlate manually or through brittle SIEM queries that break when schemas change.
Cisco's pitch: Security Cloud Control, combined with Identity Intelligence, Splunk's correlation engine, and Hypershield's enforcement, collapses this three-domain gap into single operational reality. Identity context flows into network decisions, network telemetry feeds identity risk scoring, endpoint posture adjusts access policies—continuously, correlated, actionable from unified control plane.
That's the architecture. Now let's see if it works that way.
Cisco's Approach: Three Domains, One Signal
Cisco is building toward a model where identity risk isn't calculated in isolation—it's the output of correlating three domains simultaneously:
- Authentication & Access (Duo IAM + Duo MFA): Traditional identity signals—login attempts, MFA challenges, device trust, geolocation, impossible travel detection
- Network Context (Secure Access + Hypershield): Traffic patterns, connection attempts, protocol anomalies, lateral movement indicators, microsegmentation policy violations
- Endpoint Posture (Secure Endpoint + XDR): Device health, running processes, file integrity, behavior analytics, vulnerability state
Identity Intelligence sits on top, consuming telemetry from each domain and producing continuous identity risk scores that update real-time as conditions change. Not just "user authenticated successfully" but "user authenticated and is connecting from expected network segments and endpoint posture is healthy and behavior matches historical patterns."
When something changes—endpoint posture degrades, network traffic shifts, authentication from unusual location—Identity Intelligence recalculates risk and Security Cloud Control adjusts policies accordingly. Access decisions aren't just made at login. They're made continuously, based on current context.
Security Cloud Control is the operational layer—evolved Defense Orchestrator, now positioned as control plane for Hybrid Mesh Firewall and Secure Access. Where policies get defined, where identity risk scores turn into enforcement actions, where analysts investigate correlated events without jumping between consoles.
Splunk is the data substrate underneath. Identity Intelligence is built on Splunk's correlation engine, already ingesting network telemetry (via Cisco Telemetry Broker), endpoint signals (via Secure Endpoint integrations), and authentication events (via Duo). Splunk provides the data model, query performance, and historical context that makes continuous identity risk scoring computationally feasible.
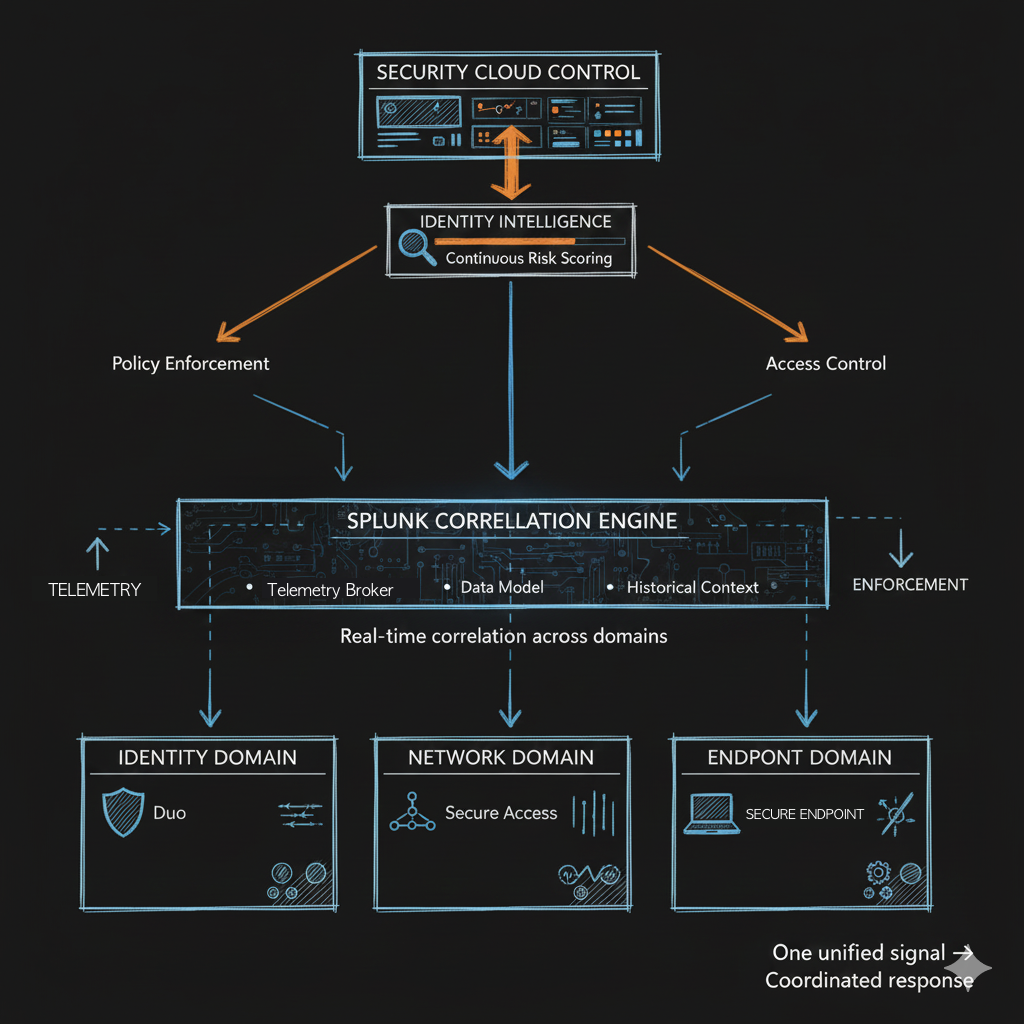
Identity Intelligence isn't another threat detection engine. It's the identity lens on top of what your XDR and SIEM already see. Your XDR detects anomalies. Your SIEM correlates events. Identity Intelligence asks: "What does this user's behavior pattern across network, endpoint, and authentication look like over time, and is this specific action right now consistent with that pattern?"
This is the architecture Cisco is building toward. The critical question: how much is shipping, integrated, and operationally proven versus roadmap aspiration?
A Scenario: When Identity Risk Changes Mid-Session
Here's what this looks like when it works:
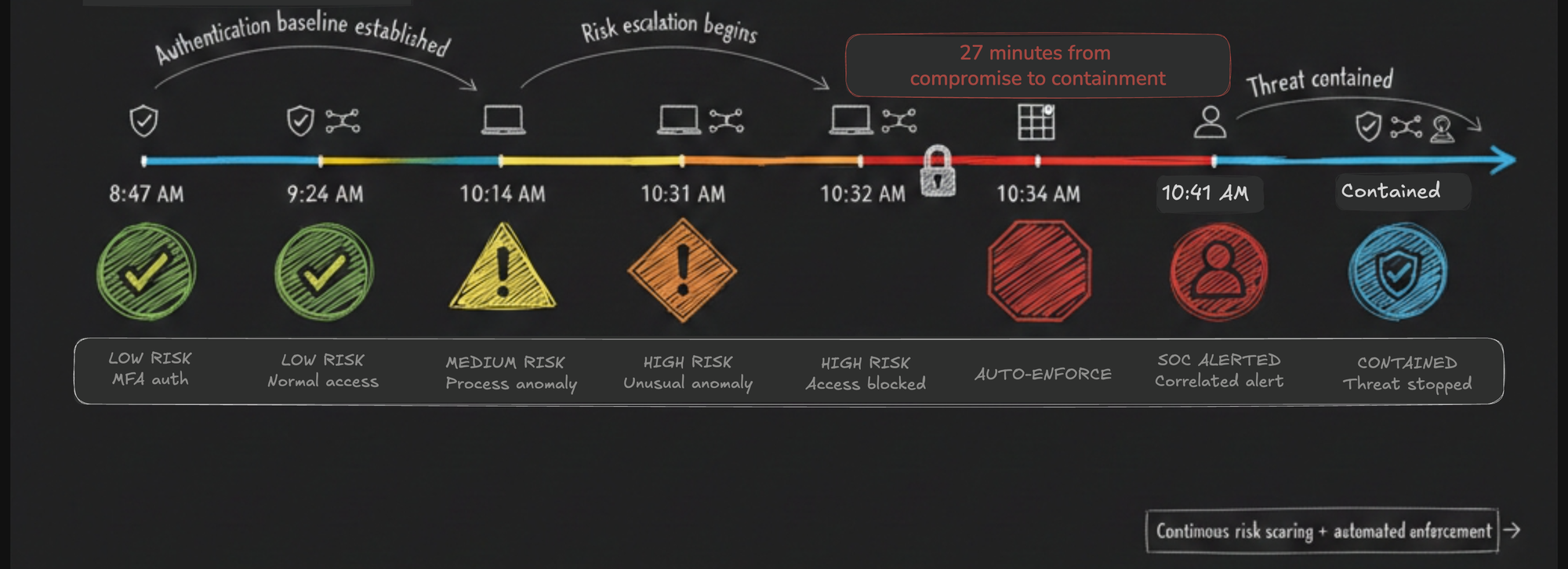
8:47 AM: Marketing manager Sarah authenticates to corporate VPN using Duo MFA. Device trust checks pass. Location matches home office. Duo IAM grants access. Identity Intelligence baseline: Low risk.
9:23 AM: Sarah accesses usual SaaS apps—Salesforce, HubSpot, internal wiki. Traffic patterns match historical behavior. Network telemetry from Secure Access shows standard HTTPS to known domains. Endpoint posture from Secure Endpoint shows healthy device. Identity Intelligence maintains Low risk.
10:14 AM: Sarah's endpoint shows new process execution—looks like legitimate productivity tool but isn't on approved software list. Secure Endpoint flags medium-priority anomaly, unusual but not malicious. Identity Intelligence updates Sarah's risk: Low to Medium.
10:31 AM: Sarah attempts to access a file share she's never touched—finance team's quarterly reports directory. Secure Access sees connection attempt. Normally allowed based on role, but Identity Intelligence now sees: elevated endpoint risk + unusual resource access + no historical pattern accessing finance data. Risk score moves to High.
10:32 AM: Security Cloud Control automatically applies policy adjustment: Sarah's access to sensitive resources suspended. She can still access normal apps, but anything high-value is blocked pending verification. Sarah receives notification: "Your access has been temporarily restricted. Please contact IT if you need assistance."
10:34 AM: SOC analyst receives correlated alert in Security Cloud Control: "User Sarah Mitchell - Identity Risk Elevated - Unusual endpoint activity + anomalous resource access." Alert includes timeline, correlated telemetry from endpoint + network + authentication, recommended actions. Analyst sees full picture in one view, not three consoles.
10:41 AM: Analyst determines Sarah's device was compromised by trojanized browser extension installed that morning. Credential theft, caught before lateral movement. Analyst uses Security Cloud Control to: (1) fully revoke Sarah's session, (2) trigger Hypershield micro-segmentation to isolate her device, (3) initiate endpoint remediation workflow. Total time from compromise to containment: 27 minutes.
What Changed?
In the old model:
- Endpoint alert happens in Secure Endpoint console. Analyst sees process anomaly but no immediate identity context.
- Finance file access attempt happens in file server logs. No automatic correlation with endpoint alert or identity risk.
- SOC analyst eventually notices both alerts, manually correlates, pulls authentication logs from Duo, checks network traffic in firewall logs, pieces together timeline over 2-3 hours.
- By the time full picture emerges, attacker has already moved laterally using Sarah's credentials.
The difference isn't detection—both models eventually catch the compromise. The difference is time compression and unified signal. Identity Intelligence + Security Cloud Control + Splunk correlation reduced investigation time from hours to minutes because all three domains were already feeding single risk calculation, and enforcement happened automatically based on policy, not manual analyst response.
A Note on Expectations: The point isn't that Cisco magically prevents all compromise. Credentials will get phished. Users will click bad links. Endpoints will get infected. The point is time compression—shrinking the window between "something's wrong" and "we know what's wrong and we're stopping it" from hours to minutes. Unified identity security doesn't eliminate threats. It eliminates the investigative lag that turns small compromises into big breaches.
What's Shipping, What's Roadmap
Let's be precise about where each piece currently stands:
Shipping & Generally Available
Duo MFA (mature, widely deployed): Multi-factor authentication, device trust, adaptive authentication policies based on geolocation and risk signals. Table stakes, and Duo does it well.
Duo IAM (launched May 2025): Full identity provider capabilities—SSO, passwordless authentication, lifecycle management. Duo IAM now supports integration with Entra Conditional Access policies and Okta Risk Signals (late 2025 preview). Important point: Cisco is not forcing identity provider lock-in. If you're standardized on Entra or Okta, Duo IAM can consume their risk signals and contribute network + endpoint context back. Most enterprises aren't ripping out existing IdPs, and Cisco knows it.
Security Cloud Control (GA mid-2025): Unified management console for Cisco security products—firewall policies, Secure Access configurations, Hypershield microsegmentation rules. Multitenant Security Cloud Control went GA November 2025, enabling MSPs to manage per-tenant identity policies from single console. Early adopters report ~40% reduction in policy deployment time across customer environments. This matters because MSPs are often the testing ground for "does this actually scale operationally?"—and early signals suggest yes.
Splunk Enterprise Security (mature platform, continuous evolution): Splunk Enterprise Security 9.2 (Q4 2025) adds real-time identity graph enhancements, including "Identity Rulebook" correlation packs and faster entity risk scoring. More importantly: Cisco Telemetry Broker is quietly becoming the preferred ingestion path for funneling Duo + network telemetry into Splunk with lower cardinality overhead. This isn't widely marketed yet, but it's the technical foundation that makes "Duo authentication event + network flow + endpoint posture → unified risk score" actually work in production without drowning your Splunk infrastructure in data volume.
Limited Availability / Early Deployment
Identity Intelligence dashboards (now available to most Duo Advantage and Premier customers as of November 2025): Real-time identity risk scoring, behavior analytics, anomaly detection correlated with network and endpoint signals. Early customers report this is where the "unified signal" story becomes tangible—seeing identity risk change real-time based on network and endpoint context is genuinely different from traditional authentication-only views.
Identity Intelligence added "Behavior Change Vectors" in October 2025—micro-pattern analysis over 24–72 hour windows detecting subtle shifts in user behavior. Not "user logged in from Russia" obvious, but "user suddenly started accessing three new SaaS apps, changed API consumption patterns, and is now connecting from a different cloud region than usual" subtle. The goal: reducing medium-risk ambiguity—those situations where nothing screams "breach!" but something feels off. This is where continuous identity security earns its keep: not catching the obvious stuff, but surfacing the quiet drift that traditional authentication-focused systems miss entirely.
Hypershield integration with Identity Intelligence (limited deployment): Automatic microsegmentation adjustments based on identity risk score changes. This is the "enforcement layer responds to identity context" piece. Early deployments show promise, still being validated at scale.
Roadmap / Announced But Not Shipping
Autonomous Response (Level 3) (Q1 2026 limited release): Cisco quietly pre-announced at a November partner summit that Autonomous Response will enter limited release Q1 2026. Identity-driven auto-suspension paired with Hypershield microsegment auto-adjustments—but only in constrained sandboxes, not full production environments. Early, limited, intentionally cautious. But if Cisco demos this at Cisco Live—even in controlled scenario—it's meaningful proof point that the integration stack is mature enough to trust with automated enforcement decisions.
Full cross-stack policy orchestration: The vision where single identity risk score change triggers coordinated responses across Secure Access, Hypershield, XDR, and SIEM—all automatically, policy-driven, auditable. Parts of this work today in limited scenarios. Full implementation across heterogeneous environments still being built.
Critical Clarity: What's Integrated vs. What's Federated
This is where most vendor stories get slippery, so let's be direct:
Genuinely integrated today:
- Duo authentication events → Splunk correlation engine (via Telemetry Broker)
- Network telemetry from Secure Access → Splunk (via Telemetry Broker)
- Identity Intelligence risk scores visible in Security Cloud Control dashboards
- Policy enforcement through Security Cloud Control based on identity risk changes (manual analyst-initiated)
Still federated / requires configuration:
- Endpoint posture from Secure Endpoint → Identity Intelligence risk scoring (integration exists but requires Splunk configuration)
- Automatic policy adjustments across firewall + access + microsegmentation based on identity risk (possible but not default)
- Unified investigation workflows across all three domains (dashboards exist, but workflow integration still requires analyst training and process changes)
Aspiration / heavily roadmap-dependent:
- Zero-touch correlation where identity, network, and endpoint signals automatically generate high-fidelity alerts with no tuning
- Fully autonomous response where policy changes happen without analyst approval
- Seamless integration with non-Cisco security tools in the stack (possible via Splunk but not natively orchestrated through Security Cloud Control)
Does This Reduce Operational Burden or Just Shift It?
Here's the test: unified identity security should reduce analyst workload, not just centralize it.
If Security Cloud Control becomes "the place where you see all your alerts from three domains in one console" but analysts still manually correlate, investigate, and decide on actions—that's console consolidation, not operational transformation. Valuable, but not revolutionary.
If Identity Intelligence automatically correlates signals, surfaces high-confidence incidents with full context, and Security Cloud Control enables one-click remediation that propagates across network, access, and endpoint enforcement—that's genuine operational leverage.
Early evidence suggests Cisco is building toward the latter, but deployment maturity varies significantly.
Cisco's 2025 Readiness Index found 31% of organizations identified identity as their top cybersecurity gap. Mandiant's M-Trends 2025 report shows median dwell time for breaches is still 10 days—attackers have plenty of time to move laterally after initial compromise if identity risk isn't continuously monitored and enforced.
Splunk's "State of Security 2025" report found identity-linked correlated alerts reduced investigation time by 44% across ~200 enterprises. That's not theoretical—measured time savings from organizations that deployed identity correlation at scale. The math is straightforward: if your analysts spend 60% of time on investigation and triage, cutting investigation time by 44% means they can handle nearly twice the alert volume with same headcount—or spend more time on proactive threat hunting instead of reactive scrambling.
"Unified identity security reduces investigation time, not the need for skilled analysts."
The promise isn't that you need fewer people. It's that the people you have can work at higher operational maturity—spending less time stitching together logs and more time understanding attacker behavior, refining policies, building resilience.
But this only works if data integration is real, Identity Intelligence correlation is accurate, Security Cloud Control policy enforcement actually propagates, and organizational alignment happens. Technology doesn't fix broken processes or siloed teams.
What to Watch for at Cisco Live EMEA
If Cisco's Security Cloud Control and Identity Intelligence story is maturing beyond architecture diagrams, Cisco Live EMEA in Amsterdam (February 2026) should provide specific proof points: live demonstrations of cross-stack correlation, customer deployment stories with operational metrics (investigation time reduction percentages, policy deployment velocity, alert volume reduction, operational headcount leverage), Splunk integration depth (Telemetry Broker architecture, actual SPL examples, data model consistency), roadmap clarity on Autonomous Response with controlled demos and scope boundaries, and customer panels discussing organizational alignment—how identity teams, network teams, and SOC worked together, what broke during deployment, how they fixed it.
If these proof points show up at Cisco Live with credible depth—real customer stories, actual operational metrics, live demos that don't feel scripted—then Cisco's "identity as correlation layer" thesis is probably real and shipping. If Cisco Live leans heavily on architecture slides, future vision, and "coming soon" messaging without operational substance, we're still in the "interesting architecture, needs another 12-18 months" phase.
Trust but Validate
Cisco's Security Cloud Control and Identity Intelligence represent a genuine architectural bet: identity security stops being a silo and becomes the correlation layer tying network, endpoint, and authentication signals into continuous risk assessment and automated enforcement.
The pieces exist. The question is integration depth. Is this genuinely unified, or "integrated" in the sense that products can exchange data if you configure them correctly and your teams know how to build the workflows?
Cisco Live will tell us. If Cisco shows up with operational proof—customer metrics, live cross-stack correlation, autonomous response demos, organizational alignment stories—then this is real. If they show up with roadmap slides and "coming soon" messaging, it's still mostly architecture aspiration.
Either way, the direction is clear: identity security is shifting from "did you authenticate successfully?" to "does your continuous behavior across network, endpoint, and authentication patterns indicate acceptable risk?" That shift is inevitable. The only question is whether Cisco's execution can deliver it in production, at scale, with operational leverage that actually reduces analyst burden.
We'll know more at Cisco Live.
Next in the Series
Networking Cloud: When Meraki and Catalyst Finally Speak the Same Language
We've examined how identity becomes the correlation layer across security domains. Now: how Networking Cloud unifies operational control across campus, data center, and cloud networking—and whether "single pane of glass" finally means something real.
Series Navigation
Read the rest of "Building Toward Amsterdam":
- Why I'm Making the Bull Case for Cisco's Transformation
- Silicon One: Why Cisco's Ethernet Bet Might Be the Smartest Play Nobody's Talking About
- Hypershield: Cisco's Bet That Security Belongs in the Data Path, Not Bolted to the Side
- Splunk: The $28 Billion Bet That Finally Gives Cisco a Data Operating System
- AgenticOps & AI Canvas: When AI Actually Understands Your Network
About this series: I'm building toward Cisco Live EMEA in Amsterdam (February 2026) by making sense of Cisco's biggest strategic moves. Part learning exercise, part knowledge sharing. I'll be hosting the broadcast again this year and want clear understanding of the storylines Cisco's building. If something resonates—or if I'm missing the mark—let's talk.

