Networking Cloud: When Meraki and Catalyst Finally Speak the Same Language
Every Cisco Live for five years: "This is the year Meraki and Catalyst speak the same language." Every year, reality was messier. November 2025 brought timelines. By Amsterdam, we'll know if it's real transformation or better co-existence.
Part of "Building Toward Amsterdam" - A public learning exercise ahead of Cisco Live EMEA 2026
Every Cisco Live for the past five years: "This is the year Meraki and Catalyst finally speak the same language."
Every year, reality was messier.
Meraki lived in the cloud with elegant simplicity. Catalyst Center ran on-premises with enterprise complexity. Different UIs, different operational models, different mental frameworks for the same problems.
Teams running both—and there are many—maintained two separate skillsets. Two dashboards. Two troubleshooting playbooks. That's operational debt.
Then June 2025 brought real progress. November 2025 brought timelines: Global Overview beta in November, GA by year-end. Cloud-managed fabric Q1 2026. Access Manager Q4 2025.
The question isn't whether the promise is real anymore. It's whether execution actually reduces operational burden—or just trades one complexity for another.
The Problem: Two Networks in Your Head
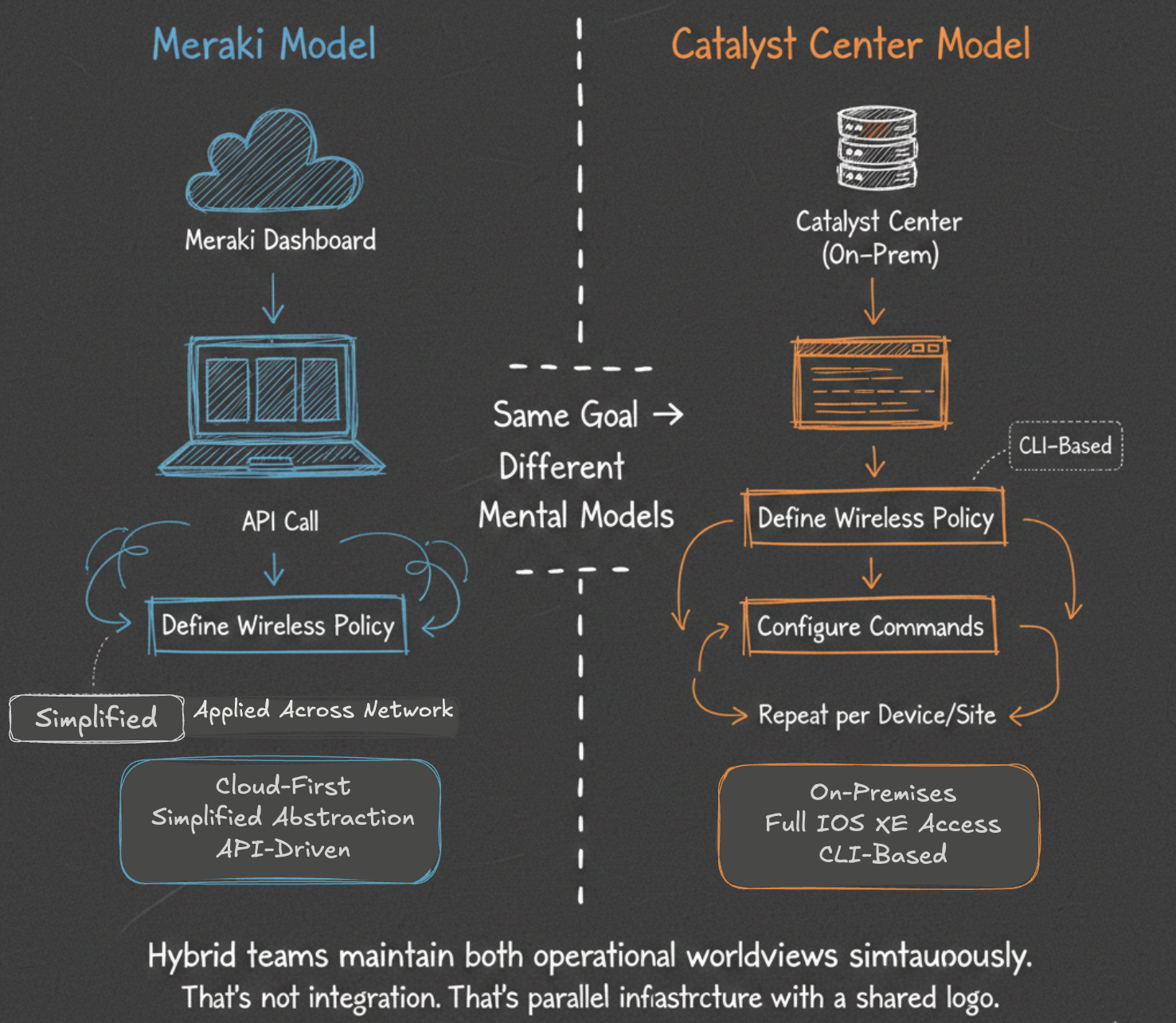
If you're running hybrid Meraki-Catalyst deployments, you're maintaining two operational worldviews.
Meraki's model: Cloud-first. Simplified abstraction—you think "wireless network" and "traffic shaping," not IOS XE syntax. API-driven extensibility. Operational assumption: simplicity over feature depth.
Catalyst Center's model: On-premises control. Full IOS XE access. CLI-based underneath. Operational assumption: enterprise-grade control justifies complexity.
A Quick Note on "Catalyst Center"
Catalyst Center is the current name for what Cisco launched in 2017 as DNA Center—the centerpiece of their intent-based networking (IBN) strategy. DNA Center brought software-defined automation to campus and branch networks, treating devices as a unified fabric rather than individual elements to configure manually.
In 2023, Cisco rebranded DNA Center as Catalyst Center, aligning it with the broader Catalyst product family. Same software, new name. The rebrand reflected Cisco's strategy to unify its networking portfolio under the Catalyst brand—hence why you'll see references to both "DNA Center" and "Catalyst Center" in documentation depending on when it was written.
For this piece, "Catalyst Center" refers to Cisco's on-premises network management platform—the system that's now being unified with Meraki's cloud management through Global Overview.
Both are valid. Neither is wrong. But they require different training, different troubleshooting, different thinking.
When you need consistent policy across both—"this security rule works whether users connect through Meraki branches or Catalyst campuses"—you write it twice. That's not unified. That's integration theater.
For mid-to-large enterprises managing 50+ sites across both platforms, this isn't a minor inconvenience. It's maintaining two entirely different mental models for the same job. Your Meraki expert troubleshoots wireless issues through elegant cloud dashboards and API calls. Your Catalyst expert SSH's into devices and runs show commands. Neither can effectively cover for the other. Security policies get written twice—once in Meraki's policy framework, once in Catalyst Center's—and inevitably drift out of sync. That's not integration. That's parallel infrastructure with a shared logo.
Cisco's November 2025 announcements don't just promise to fix this—they're shipping solutions with concrete timelines.
What's Actually Unified Now
Global Overview: One Dashboard for Everything
Global Overview launched in beta November 2025, with general availability planned before year-end—meaning it should be fully released by the time of Cisco Live Amsterdam in February 2026.
This isn't Catalyst data in Meraki styling. It's genuinely unified:
- Complete network topology: Catalyst Center campus switches, Meraki branch devices, SD-WAN routers, wireless controllers—one view
- Aggregated alerts: Cross-platform health monitoring with consistent prioritization
- Single sign-on: Authenticate once, navigate both environments without context loss
- Unified search: Find devices, troubleshoot issues, review configurations without switching dashboards
For hybrid teams, this eliminates the constant context-switching between two management paradigms. One dashboard. One authentication. One operational model.
But unification goes deeper than UI consolidation.
Cloud-Managed Fabric: Architectural Convergence
Cloud-managed fabric brings scalable architecture directly to Meraki Dashboard—fabric segmentation that normally requires Catalyst Center's complexity, now provisioned through Meraki's simplified interface. Beta Q4 2025, GA Q1 2026.
Fabric segmentation is powerful but notoriously complex: overlay networks, micro-perimeters, identity-based policies across distributed switching. Cisco's bet: Meraki's abstraction layer—why teams love it for branches—now applies to sophisticated campus deployments.
Provision advanced segmentation with clicks instead of wrestling configuration. Deploy the same fabric architecture through Meraki Dashboard that previously required Catalyst Center expertise. That's a genuine operational shift.
AgenticOps Across Both Platforms
Agentic workflow automation spans Meraki, Catalyst Center, SD-WAN Manager, ISE, Nexus—automated and orchestrated with AI Assistant. Available now.
Write a workflow once—"apply this security policy across all devices"—and it executes consistently, whether hitting Meraki cloud APIs or Catalyst Center CLI. AI Assistant understands operational intent and translates to the right enforcement point.
Real unification: not thinking about which platform manages something. Think about outcomes; the system delivers them.
Identity Fused In
Cisco Access Manager fuses identity into the network through Meraki Dashboard. Powered by ISE, optimized for cloud-managed networks, delivered as SaaS. GA Q4 2025.
Previously, identity-based access control required separate ISE integration for Catalyst; Meraki had no equivalent. Access Manager brings ISE capabilities to Meraki as SaaS.
Same identity-driven policies everywhere—Meraki branch or Catalyst campus. For teams managing identity and network access together (essential for Zero Trust), this eliminates major integration headache.
What Unified Operations Actually Delivers
For organizations managing hybrid deployments, quantifiable operational changes:
- Eliminated dual skillsets: One operational model, not two separate team specializations. New hires learn unified management, not platform-specific workflows.
- Policy consistency: Security policies written once apply everywhere. No more translating between Meraki's cloud abstraction and Catalyst's on-prem CLI.
- Faster troubleshooting: Network-wide incidents investigated through one dashboard. MTTR improvements come from consolidated visibility, not just prettier interfaces.
- Simplified automation: Workflows execute consistently without platform-specific rewrites or dual maintenance.
- Scalable operations: Adding sites or devices doesn't linearly increase management complexity.
These aren't revolutionary. They're incremental—the kind of efficiency gains that matter when managing hundreds of sites but won't transform how your team operates. Training time drops. Policy consistency improves. Troubleshooting gets faster. But you're still running complex network infrastructure that requires expertise. Unified management doesn't eliminate operational complexity; it consolidates it. Whether that's better depends on your team's skillset and how much operational debt you've accumulated running parallel systems. And there are limits to what even good unification can fix.
What Unification Doesn't Fix
- Feature differences remain: Meraki and Catalyst have different maturity areas. Unification makes managing both simpler; it doesn't erase underlying architectural differences.
- Organizational silos persist: Teams that operated separately for years have different problem-solving approaches. Tools don't automatically fix culture.
- Complexity from growth: Networks grow more complex as they scale. Unification makes that manageable, not eliminates it.
- Deep expertise still required: Advanced fabric segmentation, HA architecture, complex routing—unified UI doesn't replace technical knowledge.
Integration Across the Stack
Networking Cloud doesn't exist in isolation. It's the operational layer connecting everything else.
- Foundation layer (Silicon One, Catalyst hardware, Meraki devices, Wi-Fi 7): Purpose-built for AI workloads, generating rich telemetry
- Unified Management (Networking Cloud): Single operational plane for cloud/on-prem/hybrid, consistent policy enforcement, cloud-managed fabric simplifying campus deployments
- Visibility layer (ThousandEyes + Splunk): Network assurance across owned and unowned infrastructure, real-time correlation, telemetry flowing into unified fabric
- Operations layer (AI Assistant + AgenticOps): AI orchestrating workflows, domain-specific network understanding, automation handling routine tasks
- Security layer (Identity + SASE): Identity-based access through Meraki, SASE integrated with SD-WAN, campus-to-cloud policy consistency
The architecture depends on integration at every layer. Global Overview without ThousandEyes misses network context. AgenticOps without Splunk can't correlate incidents. Security Cloud Control without Identity Intelligence can't enforce policies. Each piece strengthens the others—or exposes gaps when missing.
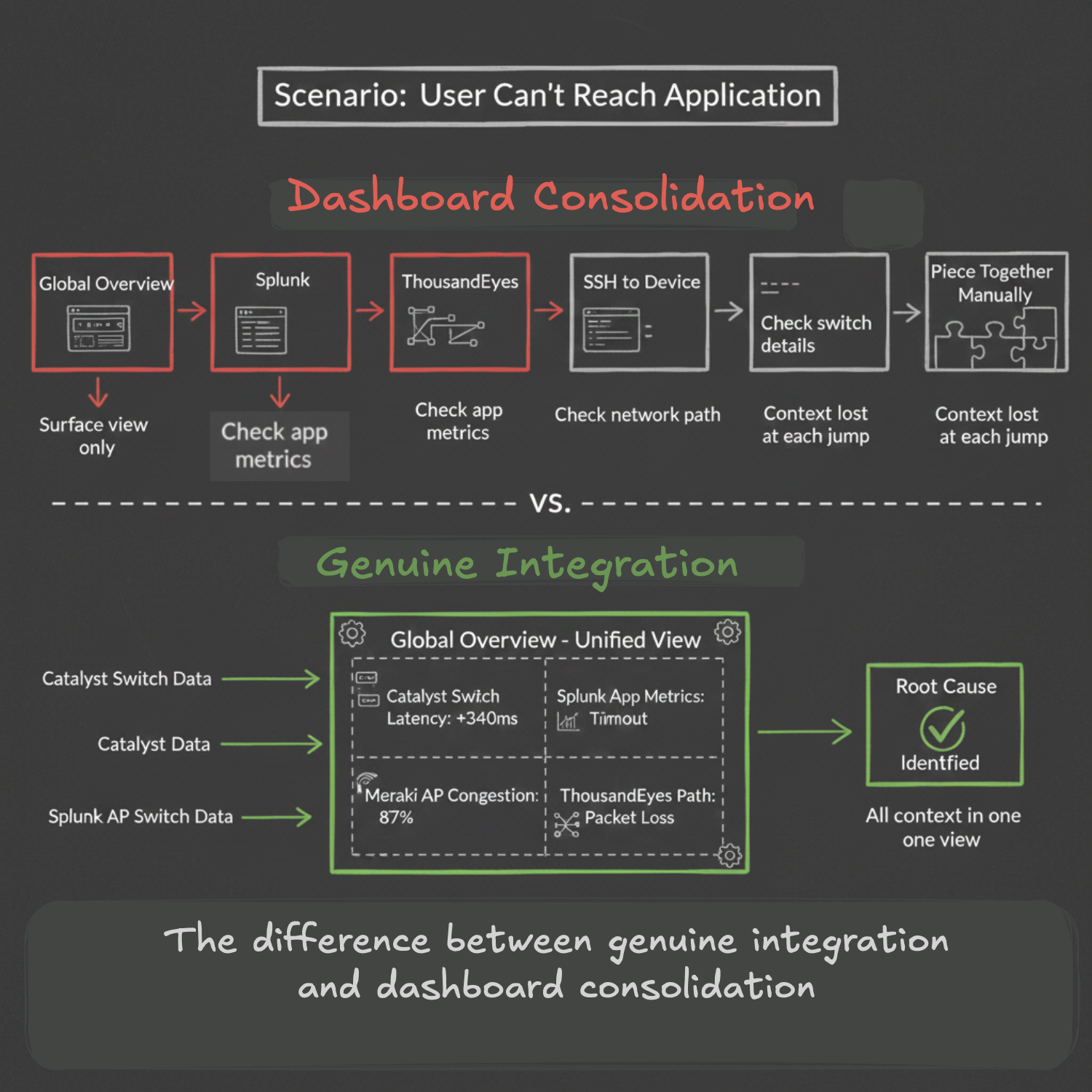
Here's the real test: when something breaks, does the integrated stack actually help you diagnose faster, or do you still end up in four separate dashboards piecing together what happened? If a user can't reach an application, does Global Overview show you "Catalyst switch latency + Meraki AP congestion + Splunk application metrics + ThousandEyes path analysis" in one view that leads to root cause? Or do you check Global Overview, then drop into Splunk, then open ThousandEyes, then SSH into something because the abstraction layer hid the detail you needed? That's the difference between genuine integration and dashboard consolidation.
This connects directly to earlier posts in the series: Hypershield's distributed enforcement works across both Meraki and Catalyst. AgenticOps workflows orchestrate consistently whether hitting cloud APIs or on-prem CLI. Splunk telemetry flows from both platforms into unified observability. Without Networking Cloud, those capabilities remain platform-specific.
What's Shipping, What's Not
| Capability | Status | Timeline | Confidence |
|---|---|---|---|
| Global Overview (unified visibility) | Beta | GA by year-end 2025 | High—shipping now, GA imminent |
| Cloud-managed fabric | In development | Beta Q4 2025, GA Q1 CY2026 | Medium-High—foundational tech proven |
| Agentic workflow automation | Shipping | Available now | Medium—works for standard scenarios |
| Access Manager (identity in Meraki) | Shipping | GA Q4 CY2025 | High—built on proven ISE, GA imminent |
| Meraki-Catalyst SSO integration | Shipping | Available now | High—straightforward interop |
| ThousandEyes-Splunk integration | Shipping | Available now | Medium—works, optimization ongoing |
| AI Assistant cross-platform workflows | Public beta | Available now | Medium—requires domain knowledge |
| Full cross-domain orchestration | Roadmap | CY2026+ | Low—vision clear, complexity being solved |
Pattern: core visibility and management unification is solid. Operations automation works for well-defined scenarios; real-world edge cases will reveal limitations. Cloud-managed fabric represents the biggest architectural shift—simplifying campus deployments through Meraki's abstraction layer while maintaining sophisticated segmentation capabilities.
Cisco Live Amsterdam Preview: Validation Tests
At Cisco Live Amsterdam (February 2026), Networking Cloud either credibly demonstrates operational unification or reveals where integration remains superficial.
Critical Scenarios to Test
Scenario 1: Unified Policy Enforcement
Define a security policy in Global Overview. Does it apply consistently whether Meraki or Catalyst enforces it? Not export/import workflows—actually unified policy management where changes propagate automatically.
Scenario 2: Cross-Platform Troubleshooting
When Meraki branch users can't reach Catalyst campus applications, does Global Overview provide one troubleshooting workflow? Or do engineers still context-switch between platforms, losing operational continuity?
Scenario 3: Brownfield Migration Path
For the thousands of enterprises running both platforms—the exact audience this matters for—what's the adoption path? Can hybrid teams gain immediate value from Global Overview without rearchitecture? This isn't a greenfield demo question; it's a "show me how existing deployments migrate" question.
Scenario 4: Cloud-Managed Fabric in Production
By Cisco Live Amsterdam, cloud-managed fabric should be in limited production. Real customer stories: Is provisioning genuinely simpler than traditional fabric? Did operational assumptions match reality? What surprised teams during deployment?
What I'm Watching For
- Live complexity demonstration: Someone managing 100+ Meraki sites and 50+ Catalyst campuses with fabric segmentation, SD-WAN across both, identity policies spanning systems. A real incident where Global Overview accelerates troubleshooting. Not sanitized—real customer, real complexity, real resolution.
- Measurable operational impact: "We reduced training time by X%." "MTTR improved Y%." "Policy deployment went from Z hours to W minutes." Specific numbers from teams migrated to Networking Cloud. Not vendor claims—actual customer experiences with timelines and context.
- AgenticOps reliability metrics: How many workflows running in production across hybrid environments? Success rates for cross-platform orchestration? Where do they fail? What scenarios still require manual intervention? Honest operational data.
- Integration depth validation: Is Meraki-Catalyst integration truly deep or primarily UI-level? Can admins deploy fabric with identity-based segmentation and SASE policies through one workflow, or do they drop to lower levels for finalization? The test: Does "unified" mean consistent operational model or just consolidated dashboard?
- Competitive differentiation: How does this differ from Arista, Juniper, or HPE+Mist unified management? Cisco's advantage should be breadth—managing cloud and on-prem simultaneously with consistent operational model across campus, branch, data center. If that's not clearly articulated against competition, the differentiation claim weakens.
Trust Validation: Simple vs. Simpler
Does unified management actually make networks simpler to operate, or just simpler to think about?
Both, but differently.
- Simpler to think about: One dashboard, one authentication, one conceptual model. Absolutely.
- Simpler to operate: Depends whether underlying complexity decreases or just hides better. For routine tasks—provisioning, standard troubleshooting, applying policies—yes, simpler. For advanced scenarios—debugging complex segmentation, optimizing cross-platform performance, handling edge cases—you still need deep expertise.
Real test: Do customers who adopt Networking Cloud free experienced engineers for higher-value work, or just move them from 'manage two dashboards' to 'manage one dashboard hiding the same complexity'?"
Cisco Live Amsterdam clarifies this when we hear from customers running it for months, not weeks.
What Would Prove This Is Real
If Cisco demonstrates at Cisco Live Amsterdam that:
- Global Overview enables faster cross-platform troubleshooting with measurable MTTR improvements in hybrid environments
- Customers use cloud-managed fabric in production with demonstrated simplification over traditional deployment
- Identity policies apply seamlessly across Meraki and Catalyst without platform-specific tuning or translation
- Workflows reduce operational tasks with quantified time savings, not just easier-to-understand interfaces
- Organizations reduce operational overhead with specific metrics—training time, deployment speed, policy consistency
Then Networking Cloud stops being a promise and becomes operational reality.
If any element is missing or overstated, we're still in the same pattern Cisco's followed for five years: announcing unification at Cisco Live, delivering better co-existence, and asking customers to wait for the next release. Good progress isn't the same as delivered transformation. By Amsterdam, we'll know which one this is.
Next in the Series
The Synthesis: How the Storylines Converge at Cisco Live Amsterdam
We've examined Silicon One, Hypershield, Splunk, AgenticOps, Security Cloud Control, and Networking Cloud. Now: connecting the dots. Where are these pieces genuinely integrated, and where is integration still aspirational? What does success look like, and what proves Cisco's transformation is real?
About this series: I'm building toward Cisco Live Amsterdam (February 2026) by making sense of Cisco's biggest strategic moves. Part learning exercise, part knowledge sharing. I'll host the broadcast again this year and want clear understanding of the storylines Cisco's building. If something resonates—or if I'm missing the mark—let's talk.

