Hypershield: Cisco's Bet That Security Belongs in the Data Path, Not Bolted to the Side
Cisco Hypershield challenges a core assumption: that security happens at the perimeter. With eBPF-based agents, DPU offloading, and enforcement embedded in smart switches, it moves security into the data path itself—where AI workloads actually need it. The question is whether Cisco can execute.
Part of "Building Toward Amsterdam" - A public learning exercise ahead of Cisco Live EMEA 2026
What if your entire security model is based on an assumption that stopped being true five years ago?
The assumption: Most traffic flows north-south, through defined perimeters where you can inspect it.
The reality: AI workloads, microservices, hybrid cloud—most traffic today flows east-west between servers, containers, and GPUs. By the time it reaches your perimeter firewall, the damage is already done.
First announced in April 2024, Cisco unveiled Hypershield with a tagline that landed like a challenge: "The most radically different security innovation" in the company's history. At Cisco Live EMEA earlier this year, the platform reached a major milestone with the launch of DPU-enabled Nexus 9300 Smart Switches that embed security directly into the network fabric. Tom Gillis, SVP of Cisco Security, wasn't overselling. I've heard him present at multiple Cisco Live events, and this is the first time I've seen him lead with a claim this bold. This isn't another next-gen firewall. It's a fundamental rethinking of where security enforcement happens.
Let me show you why this matters—and why the technology foundation actually makes it credible.
The Problem: Hairpinning Traffic Doesn't Scale
Let's start with what's broken.
Traditional security creates chokepoints. You route traffic through firewalls, IPS appliances, or virtual security functions. This made sense when your data center had clear boundaries and most traffic crossed them.
But modern infrastructure doesn't work that way anymore.
An AI training cluster might have 1,000 GPUs exchanging terabytes of data between nodes for model synchronization. A microservices application might have dozens of containers communicating constantly within the same host. A hybrid cloud deployment might have workloads spanning on-premises data centers, AWS, Azure, and Google Cloud—with traffic patterns that change based on load balancing and auto-scaling.
When you try to backhaul all that traffic through centralized security appliances, you create bottlenecks. The network design becomes constrained by security topology rather than performance optimization. And you still miss threats because most of the interesting attack surface—lateral movement between workloads—never touches your perimeter.
As Craig Connors, Cisco's VP and CTO of Security, explained to me in conversation: In modern enterprises spanning private data centers, public cloud, BYOD, and IoT, centralized enforcement is inefficient because traffic must be shuttled to and from enforcement points. The answer is distributing enforcement close to the workload.
This isn't just an architecture problem. It's an AI-era problem.
AI infrastructure generates massive east-west traffic flows. Training workloads need lossless, low-latency communication between GPUs. Inference workloads need ultra-fast response times. Traditional security models that introduce latency and complexity in the data path simply don't fit.
The Hypershield Answer: Security Lives Where the Data Flows
Here's Cisco's bet: Instead of routing traffic to security, bring security to the traffic.
Hypershield distributes enforcement using multiple form factors, each optimized for where it sits in the infrastructure:
Tesseract Security Agent - Software running directly on endpoints (VMs, Kubernetes pods) using eBPF (extended Berkeley Packet Filter) for kernel-level visibility and control. This agent sees everything: network packets, file operations, process behavior, system calls.
DPU Integration - Offloading security to Data Processing Units in the server itself, handling enforcement in hardware without burdening the CPU. Hypershield supports AMD Pensando DPUs, initially available in Cisco UCS servers and other leading vendor platforms.
Smart Switches (DPU-Enabled Fabric) - Cisco Nexus 9300 Series switches with embedded DPUs that can enforce stateful Layer 4 security policies and microsegmentation directly at the network fabric level. The switches are available now in networking mode, with Hypershield L4 segmentation features targeted for an upcoming release.
Silicon One ASICs - Long-term vision: security enforcement directly in the switching silicon, inspecting and blocking threats at line rate.
The key architectural principle: Centralized policy, distributed enforcement.
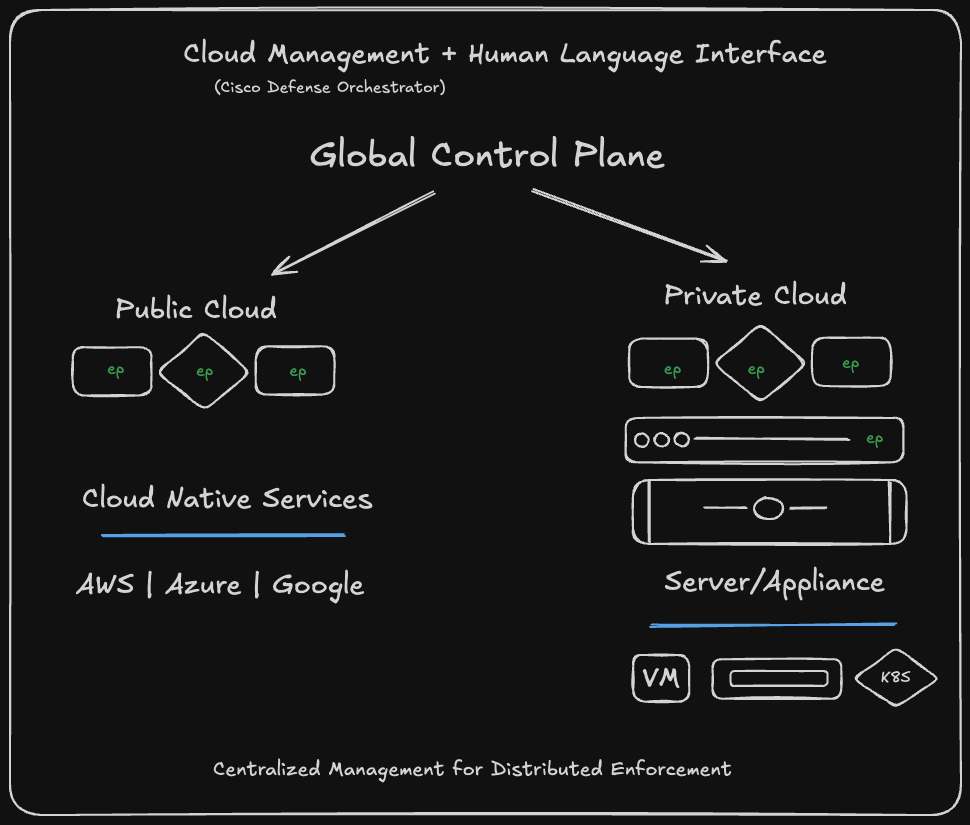
No matter where enforcement happens—agent, DPU, switch, or ASIC—policy is managed from a single control plane (Security Cloud Control). When you create or update a policy, it gets compiled and intelligently distributed only to the enforcement points that need it.
Think of it as pushing the firewall down to where the workload actually lives. Micro-segmentation at the process level, not just the network level.
The eBPF Foundation: Why This Is Credible
Let's talk about what makes this technically feasible, because "distributed security" has been promised before and mostly failed.
The difference: eBPF.
eBPF is an open-source technology that lets you run programmable logic in the Linux kernel without modifying kernel code itself. It's become the de facto standard for high-performance, non-invasive visibility and security in hyperscalers.
Meta uses it. Google uses it. Netflix, Datadog, Cloudflare—all the cloud-native infrastructure companies rely on eBPF for observability and security because it works at kernel level with minimal overhead.
Cisco acquired Isovalent—the team behind Cilium, the leading eBPF-based networking and security project—and they're stewarding it as open source while building commercial orchestration layers on top.
This matters because it's not proprietary Cisco magic. It's proven technology that's already running at massive scale in production environments. Cisco's industrializing it for enterprise use with centralized management and policy consistency.
What eBPF enables in Hypershield:
Deep visibility - The Tesseract Security Agent can see process relationships, file operations, network connections—everything happening inside a workload. It builds an application behavior graph showing how processes interact, what files they access, which network connections they open.
Precise enforcement - Policies can be applied not just by IP and port, but by process, binary, and in-memory behavior. You're not just blocking "traffic to port 443"—you're blocking "this specific process attempting to open an unexpected network connection."
High performance - eBPF executes policies efficiently with minimal overhead. It's safe for production systems because it runs in a sandboxed environment within the kernel.
Dynamic adaptation - Hypershield learns application behavior over time. As workloads evolve, it can recommend policy adjustments based on observed patterns rather than requiring manual updates.
This is the technology foundation that makes distributed security actually work at scale.
The Autonomous Piece: AI That Earns Trust
Here's where it gets interesting—and where Cisco had to be careful not to over-promise.
Hypershield has AI-driven capabilities, but they've architected it to build trust incrementally rather than demanding blind faith in autonomous security.
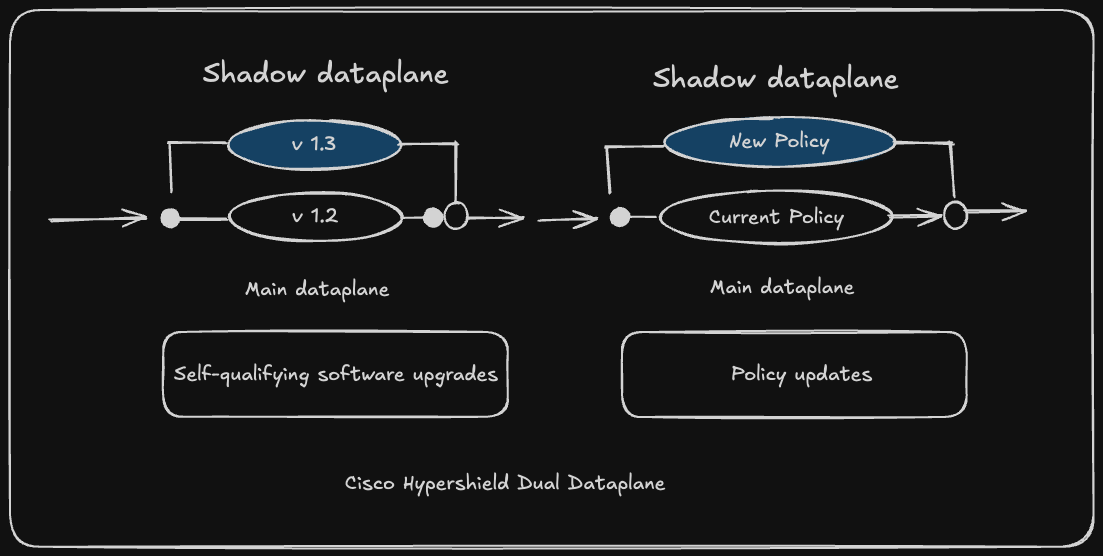
The dual dataplane approach:
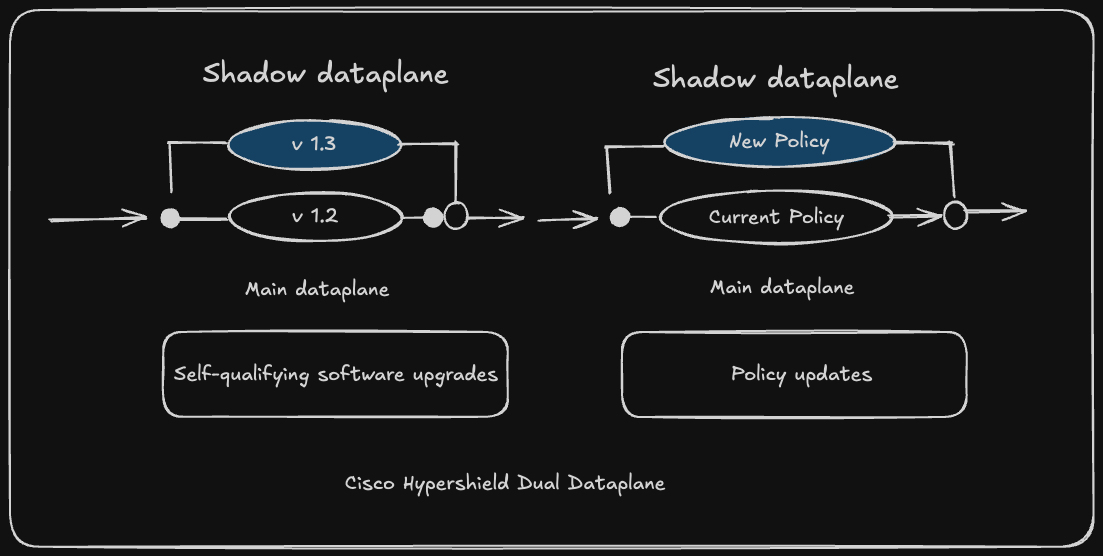
Hypershield runs two parallel data paths—primary (production) and secondary (shadow). Updates and policy changes are first applied to the shadow dataplane, tested against live traffic, and validated before being promoted to production.
This turns security updates from high-risk change control events into routine, non-disruptive operations. The system continuously tests itself against real traffic patterns, measures effectiveness, and only promotes changes when confidence is high.
Application behavior learning:
By watching process relationships and workload activity through eBPF, Hypershield builds a fingerprint of normal behavior. When applications update or workflows change, it can detect the shift and suggest policy adaptations.
The key: It suggests, you approve. The autonomy level is adjustable—you can set how much the system does automatically versus requiring human validation.
Distributed exploit protection:
Hypershield can identify vulnerabilities in your environment and deploy compensating controls automatically—blocking attack paths before patches are available, sometimes even before you know about the vulnerability.
This is the "autonomous segmentation" vision: The system draws defensive boundaries based on observed behavior, tightening policies progressively from macro-level guardrails down to specific regex filters, all without manual intervention.
But—and this is critical—Cisco built it to earn trust through transparency. You can see what it's doing, why it's doing it, and override decisions. The "AI-powered" label isn't magic; it's applied machine learning with clear explainability.
The Deployment Reality: Starting Simple, Scaling Smart
Let's talk about how this actually gets deployed, because distributed security sounds conceptually elegant but operationally terrifying.
Cisco's being pragmatic about the roadmap:
Phase 1 (Generally Available as of August 2024): Tesseract Security Agent on Linux VMs and Kubernetes environments. This is the eBPF-based software deployment where the technology is most mature. You can start with visibility—just watch what's happening—before enforcing policies.
Phase 2 (Targeted late 2024): DPU integration with AMD Pensando DPUs, initially available in Cisco UCS servers and other leading vendor platforms. This offloads enforcement to hardware accelerators in the server, improving performance and reducing CPU overhead.
Phase 3 (In progress): DPU-enabled Nexus 9300 Smart Switches with Hypershield L4 segmentation, enforcement at the network fabric level. Then eventually full Silicon One ASIC integration for line-rate inspection in the switching silicon itself.
The strategy: Start where eBPF already works, prove value with agents, then expand to hardware acceleration as those capabilities mature.
The management story:
Security Cloud Control provides the centralized policy framework. You define intent-based policies—"application X should only communicate with database Y"—and Hypershield compiles that into enforcement rules distributed to the appropriate agents, DPUs, or switches.
From the admin perspective, you're managing one security fabric with unified policy, even though enforcement is distributed across potentially thousands of points.
Integration with existing security:
Hypershield isn't rip-and-replace. It integrates with Cisco's existing security portfolio:
- Feeds telemetry to XDR for threat detection and correlation
- Works with Secure Firewall for perimeter defense (handling different threat vectors)
- Integrates with Duo for identity-based policy enforcement
- Sends data to Splunk for unified observability and analytics
The pitch: Start with Hypershield for east-west microsegmentation and exploit protection, keep your existing tools for north-south perimeter defense and identity/access control. Over time, the distributed fabric handles more of the enforcement workload.
Why This Approach Fits AI Infrastructure
Let's connect this back to the broader Cisco transformation story.
AI infrastructure has specific security requirements that traditional models can't meet:
Performance sensitivity: Training workloads can't tolerate the latency of hairpinning traffic through centralized inspection. Hypershield enforces policies locally without adding hops or bottlenecks.
Dynamic topology: AI clusters scale up and down based on workload. Containers spawn and terminate constantly. Hypershield's agent-based model follows workloads wherever they move—on-premises, to public cloud, across hybrid environments.
East-west dominance: In an AI training cluster, 80-90% of traffic never leaves the rack or pod. It's GPU-to-GPU communication for gradient synchronization. Perimeter security misses it entirely. Hypershield secures it at the source.
Rapid vulnerability patching: AI frameworks (PyTorch, TensorFlow) and supporting libraries update frequently. Hypershield's distributed exploit protection can deploy compensating controls while patches are being tested and rolled out.
This is why Tom Gillis called it security "reimagined for AI-scale data centers." It's not that traditional security doesn't work—it's that it doesn't scale to the traffic patterns and performance requirements of modern infrastructure.
The Open Source Play: Cilium as Strategic Asset
Here's a piece of the story that matters more than it seems at first glance.
Cisco acquired Isovalent, but they kept Cilium—the underlying eBPF networking and security platform—open source. They're actively contributing to it, building the community, and ensuring it remains vendor-neutral.
Why does this matter?
Ecosystem credibility: By keeping Cilium open, Cisco benefits from community innovation. Contributions from Google, Meta, AWS, and other hyperscalers improve the technology that Hypershield is built on. It's not a Cisco-only project that stagnates.
Interoperability: Enterprises can use Cilium directly (open source) or use Hypershield (commercial orchestration and management). This "open core" model reduces lock-in fear and lets customers start with open source before buying commercial features.
Talent pipeline: The Cilium community is large and growing. By aligning Hypershield with a technology that cloud-native engineers already know, Cisco makes adoption easier. There are books, courses, certifications—educational infrastructure that Cisco didn't have to build.
This is strategic positioning: Cisco's not fighting the cloud-native ecosystem; they're participating in it and adding value on top.
What's Missing: The Honest Limitations
Let me be clear about what Hypershield doesn't solve yet, because nuance matters.
Operational complexity risk: Distributed enforcement across agents, DPUs, and switches sounds elegant in theory. In practice, troubleshooting becomes harder. "Why was this connection blocked?" now requires understanding which enforcement point made the decision and why.
Cisco's response: Centralized policy via Security Cloud Control means all decisions flow from the same intent-based rules, and unified telemetry through Splunk integration provides a single pane of glass for forensics. The bet is that logical simplicity (one policy framework) overcomes physical complexity (many enforcement points). We'll see if that holds in production.
Performance overhead: eBPF is efficient, but it's not free. Running security logic in the kernel consumes CPU cycles. On workloads that are already resource-constrained, this could matter.
Cisco's response: DPU offload (AMD Pensando in UCS and partner servers) and the roadmap to Silicon One ASIC integration are specifically designed to eliminate CPU tax. The question is adoption timeline—DPUs add cost, and ASIC enforcement is still future roadmap.
Policy modeling complexity: Intent-based policies are great until you have to define intent for complex, legacy applications that weren't designed with microsegmentation in mind. The "learning mode" helps, but migrating brownfield environments to zero-trust microsegmentation is still operationally hard.
Hardware dependency timeline: The full vision—security embedded in Silicon One ASICs, enforcement at line rate in the switch—that's future roadmap. Today, it's software agents and DPUs with Smart Switch L4 segmentation coming soon. The hardware acceleration story is compelling but not yet fully realized.
Integration maturity: Hypershield feeding telemetry to XDR, correlating with Splunk, coordinating with Duo—these integrations are rolling out in phases. The "unified security fabric" exists more as architecture than as shipping product in some areas.
These aren't fatal flaws. They're execution risks. Cisco's betting they can navigate them, but enterprises should go in eyes-open about what's mature versus what's roadmap.
Amsterdam Preview: What I'm Watching For
At Cisco Live Amsterdam, here's what I'll be watching for—and what I plan to press Cisco's security team on when I'm there:
Customer deployments with metrics: Not "we're piloting Hypershield" but "we deployed it across 5,000 workloads and reduced lateral movement incidents by X% while improving application performance by Y%." Real numbers, real environments.
DPU integration timeline: When does hardware offload actually ship at scale, and with which server vendors beyond UCS? This is the bridge between "software-based" and "silicon-embedded" security.
Smart Switch performance in production: Real-world demonstrations of L4 segmentation running at line rate on Nexus 9300s with Hypershield enabled. Can it enforce microsegmentation policies on AI training traffic without introducing latency?
Brownfield migration stories: How are customers with complex legacy environments actually implementing microsegmentation? What's the operational playbook for going from "learn mode" to "enforce mode" without breaking applications?
XDR + Splunk correlation depth: Show me a live demo where a Hypershield agent detects anomalous behavior, correlates it with XDR threat intelligence and Splunk network telemetry, and triggers automated response. The integration story needs proof.
Performance benchmarks: Overhead measurements for AI training workloads running with Hypershield enabled. If it adds 5% latency to GPU synchronization, that's a problem. If it's sub-1%, that's compelling.
The technology foundation is solid—eBPF is proven, the architecture is sound, the team from Isovalent knows what they're doing. The question is execution at Cisco scale, integration with the broader portfolio, and operational simplicity in real-world deployments.
How This Fits the Transformation Puzzle
Step back and look at where Hypershield sits in Cisco's overall strategy:
Silicon One provides high-performance networking for AI infrastructure.
Hypershield secures that infrastructure with distributed enforcement.
Splunk correlates Hypershield telemetry with network, application, and security data.
Security Cloud Control provides unified policy management across distributed enforcement points.
XDR detects threats using telemetry from Hypershield and other sources.
AgenticOps layers AI-driven automated response on top of the security fabric.
It's a stack. Each piece reinforces the others.
Hypershield isn't just a product—it's the manifestation of Cisco's "security embedded everywhere" vision. And it only works because the rest of the infrastructure transformation is happening in parallel.
The Bottom Line
Here's what Cisco's actually saying with Hypershield: The perimeter is dead. Accept it and build security for the world that actually exists—distributed workloads, hybrid infrastructure, AI-scale east-west traffic.
The technology bet—eBPF-based distributed enforcement with centralized policy—is credible. It's proven at hyperscale, it's being industrialized for enterprise, and the roadmap from software to hardware acceleration is logical.
The execution bet—integrating this with XDR, Splunk, Security Cloud Control, and Duo into a unified fabric—that's harder to call. Integration is where Cisco acquisitions historically stumble.
But if they pull it off? Security finally catches up to how infrastructure actually works. Microsegmentation becomes operationally practical. Zero-trust becomes more than a buzzword. And enterprises get defense that scales with AI workloads instead of constraining them.
That's not incremental improvement. That's the architectural shift the industry needs.
Now Cisco just has to execute.
Your Take?
Are you running distributed workloads where traditional perimeter security doesn't cut it? Does the Hypershield approach—enforcement at the workload level using eBPF—solve real problems you're facing, or create new operational complexity?
And if you're in security architecture: Is microsegmentation with distributed enforcement the future, or are we overcomplicating what should be simple perimeter defense?
I'm especially curious to hear from anyone running AI infrastructure: Does security enforcement in the data path work with the performance requirements of GPU-to-GPU communication, or does any inspection/enforcement create unacceptable latency?
I'm headed to Amsterdam to see how much of this vision has shipped versus how much is still roadmap. If you're planning to be there—or if you're already running Hypershield in production—I'd love to hear what you're seeing.
Sources and Further Reading
- Cisco Hypershield eBook - Architecture and Use Cases (pdf)
- Cisco Live EMEA 2025 Session Recordings (Hypershield Deep Dives)
- Security Cloud Control
- Cisco Nexus 9300 Series Smart Switch Data Sheets
eBPF and Cilium:
- The Cilium Project (cilium.io) - Open source eBPF-based networking and security
- eBPF.io - Community hub for eBPF technology and use cases
- Isovalent Blog - Technical deep dives from the Cilium team (now part of Cisco)
Next in the series: The Splunk Integration story—how a $28B acquisition becomes the data substrate that makes everything else (Hypershield telemetry, AgenticOps intelligence, unified observability) actually possible.

