Air-Gapped by Design: Cisco's Sovereign Infrastructure Bet
Cisco just made on-premises expertise a growth market again. The Sovereign Critical Infrastructure portfolio runs entirely air-gapped—Cisco cannot access it, even if governments demand. For specialists who maintained air-gap expertise while the industry chased cloud? Vindication.
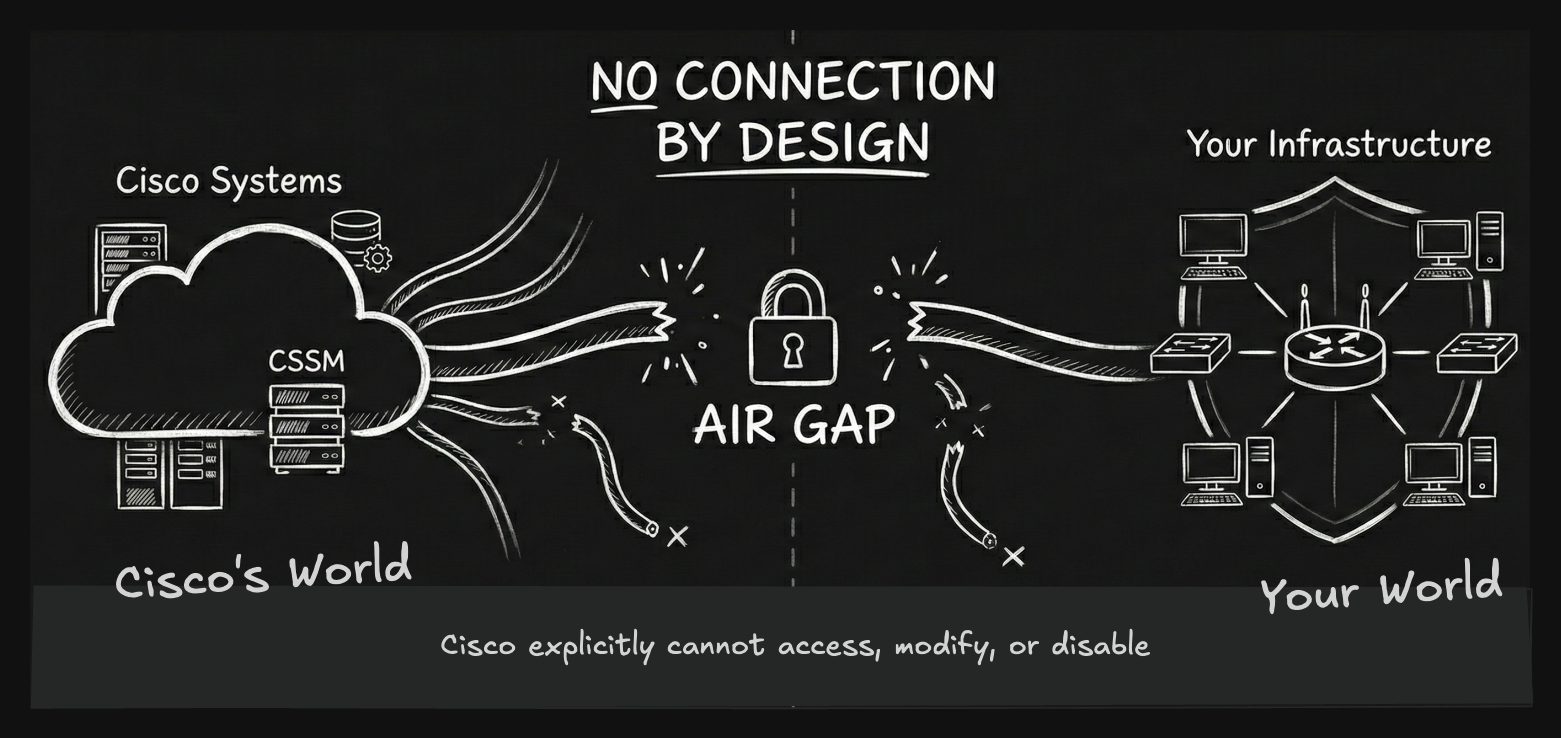
In September 2025, Cisco announced something that would have been unthinkable five years ago: a portfolio of networking products designed to never connect to the internet. Not "occasionally disconnected." Not "edge-deployed with intermittent connectivity." Never. By design.
The Sovereign Critical Infrastructure portfolio runs entirely air-gapped. No license callbacks to Cisco's cloud. No telemetry. No remote management. No ability for Cisco to disable products or push updates. Once deployed, these systems are entirely under customer control—and Cisco explicitly cannot access them, even if governments demand it.
This isn't a niche offering for paranoid customers. It spans routing, switching, wireless, collaboration, security, and observability—Cisco's core product lines. It's a strategic reversal that validates what specialist integrators have been saying for years: in an era of digital sovereignty and geopolitical tension, air-gapped infrastructure isn't legacy architecture waiting to be deprecated. It's the only acceptable option for critical infrastructure.
Why Standard Cisco Doesn't Work for Sovereignty
I've spent the past year working with VQ Communications on sovereign collaboration systems for defense and government customers. I've watched specialist integrators build workarounds for Cisco products that assumed connectivity, maintaining air-gap expertise while the industry mocked them as dinosaurs refusing to embrace cloud transformation.
Standard Cisco infrastructure has a fundamental problem for sovereign environments: it's designed to stay connected.
Traditional Cisco products use Smart Licensing that requires regular check-ins with Cisco's cloud for license validation. Even with on-premises license servers, there's synchronization with Cisco. For classified environments with zero internet access, that's architecturally unacceptable. Every connection is a potential attack vector.
Remote control violates sovereignty. Traditional Smart Licensing meant Cisco retained theoretical ability to remotely disable products or push updates. For governments asserting control over critical infrastructure, that capability—however unlikely to be exercised—represents a sovereignty violation. Europe wants infrastructure truly under its control: no external entity can access, modify, or terminate operations.
Between Cisco's cloud-first strategy and government requirements for air-gapped sovereignty, a gap emerged. Specialist integrators filled it—building management platforms that operate entirely on-premises, obtaining security clearances for classified environments. For years, these partners operated in tension with Cisco's product roadmap. Every new feature assumed cloud connectivity. Every licensing simplification made air-gap deployments harder.
September 2025 changed that calculation.
What Cisco Actually Announced: An Inverted Operational Model
The Sovereign Critical Infrastructure portfolio leverages Specific License Reservation (SLR)—permanent license assignments requiring no ongoing communication with Cisco. Devices generate request codes that you manually take to Cisco's cloud via a connected system, reserve specific licenses permanently against that hardware, then install authorization codes back on air-gapped devices. Once installed, the license never expires and requires no further contact with Cisco.
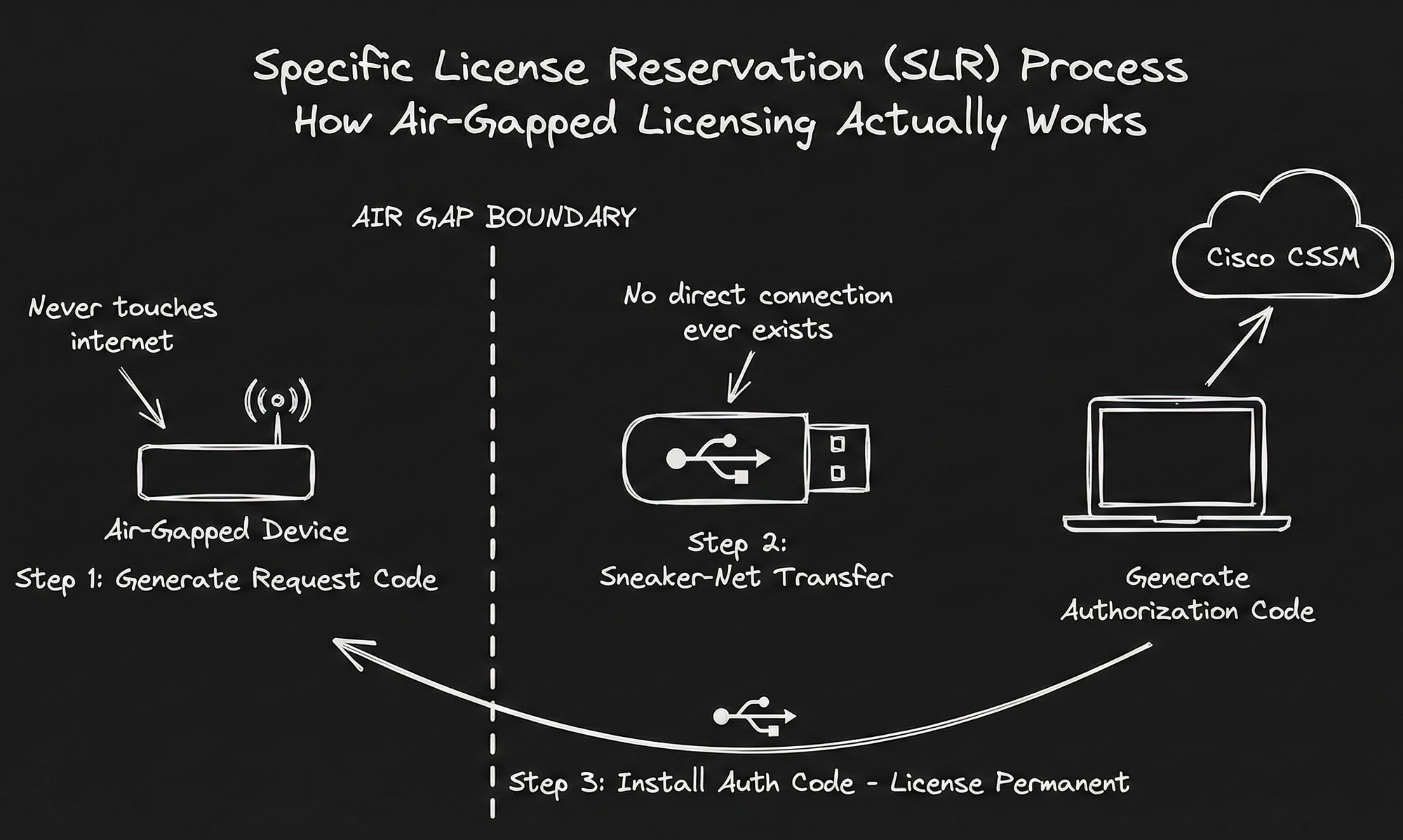
This isn't new hardware—it's new licensing for existing products. What's revolutionary is Cisco committing to support products that never call home, with no Cisco access and no Cisco control once deployed. That commitment inverts the operational model. With traditional Smart Licensing, Cisco retained visibility and control. With SLR for sovereign infrastructure, Cisco cannot provide customer data in response to government demands or remotely impair operations. Control is entirely in customer hands.
The portfolio spans core infrastructure: Catalyst switching and routing, wireless controllers and access points, Cisco Meeting Server and collaboration endpoints, security appliances, and Splunk observability. Notably absent: Meraki. Cloud-native platforms don't translate to air-gapped deployments.
If your network runs on Meraki, sovereign infrastructure requires forklift replacement with Catalyst Center-managed alternatives. That's not a licensing change—it's a multi-year migration project redesigning campus architecture, retraining staff, and managing parallel infrastructure during transition.
Customers can configure bespoke security—customer-managed encryption keys, custom hardening, organization-specific compliance policies—and deploy in hybrid environments with critical workloads air-gapped while non-critical systems stay cloud-connected.
But sovereign infrastructure isn't plug-and-play. You're buying hardware, reserving licenses manually, configuring custom security policies, implementing bespoke encryption, documenting every deviation from baseline, and sustaining that environment without cloud automation. Sovereign infrastructure trades operational simplicity for absolute control.
Products are Common Criteria certified today. European Union Cybersecurity Certification (EUCC) certification became available in February 2025, with the scheme receiving its second amendment in December 2025. Cisco's sovereign portfolio will need EUCC certification to fully satisfy European regulatory requirements—watch for which products receive certification and on what timeline. The scheme exists and is operational; the question is execution speed for vendor adoption.
Why This Matters: Strategic Reversal and Market Validation
For a decade, Cisco's strategy assumed connectivity. Products were designed cloud-first, with on-premises as compatibility mode. Management platforms prioritized SaaS delivery. Licensing required internet access or elaborate workarounds.
September 2025 made air-gapped deployments a first-class architecture, not a workaround. Digital sovereignty isn't a compliance trend Cisco can wait out—it's a market requirement reshaping product roadmaps.
The competitive distinction matters. Microsoft and AWS launched digital sovereignty services with Euro-centric cloud offerings, but their approach differs fundamentally. They can promise not to access infrastructure, but they can't remove the capability—their platforms are designed with centralized management built-in. Cisco's approach: infrastructure that physically cannot be accessed remotely because it never connects outside customer control. Not "we promise not to look"—it's "we physically cannot look."
Geopolitical context extends beyond Europe: the U.S. Department of Defense's CMMC increasingly requires defense contractors to demonstrate infrastructure control. Australia's Critical Infrastructure Act and Singapore's Cybersecurity Act implement sovereignty requirements for critical sectors. Gulf states investing in national digital infrastructure want absolute control over systems managing oil production and power grids.
AI infrastructure drives urgent demand. Training large language models requires massive datasets containing proprietary information, personal data, or classified research. Running those workloads on cloud infrastructure where hyperscalers can theoretically access data—where foreign governments can demand access, where model weights transit networks you don't control—introduces unacceptable risk. Air-gapped training environments aren't paranoia for healthcare AI, financial fraud-detection models, or defense research. They're the only defensible architecture.
Here's Cisco's strategic bet: As AI becomes infrastructure, sovereign control becomes mandatory. Today that's governments and research institutions. Tomorrow it's banks, hospitals, and manufacturers.
For specialist integrators, September 2025 was vindication. Companies focused on secure communications for defense and critical infrastructure—who maintained on-premises expertise while the industry chased cloud revenue—suddenly found their niche becoming mainstream.
And they're already moving. VQ Communications just announced licensing solutions to support Cisco collaboration endpoints in air-gapped DoD environments—specifically handling the gaps Microsoft's Teams Rooms Pro Management portal can't address in classified settings. That's not "waiting for Cisco's roadmap to clarify." That's building the sovereign ecosystem today.
Cisco sells hardware and licenses. Partners deliver design, integration, hardening, compliance documentation, and sustained operations. Success depends on formal partner certification programs, widely available training, and economics that let specialists build sustainable businesses.
Where This Could Fail
Sovereign infrastructure solves the control problem but creates operational problems. Traditional air-gapped network management is manual and labor-intensive. You can't phone home for support. Security patches that cloud systems receive automatically become multi-day projects requiring change control, manual transfers, individual device installation, and compliance documentation.
Cisco Catalyst Center (formerly DNA Center) does support air-gapped deployments with on-premises automation for configuration, provisioning, and policy management. But even with Catalyst Center, the update process remains manual—you're still raising TAC requests, downloading images to connected systems, transferring via USB or isolated networks, and executing upgrades individually. The automation exists within the air-gapped environment, but getting updates into that environment is sneaker-net by design.
Cisco IQ is the next-generation answer—but the timing is problematic. Announced at Partner Summit in November 2025, Cisco IQ is AI-powered management with three deployment modes: SaaS, on-prem tethered, and on-prem air-gapped. The air-gapped version packages Cisco's AI models, troubleshooting knowledge base, and compliance frameworks into a deployable VM that provides infrastructure insights without data leaving your environment.
The problem: Cisco IQ is currently in Early Field Trials, with general availability planned for late 2026. We won't see mature sovereign infrastructure with integrated AI management in the short term. We'll see announcements, demos, maybe early trials.
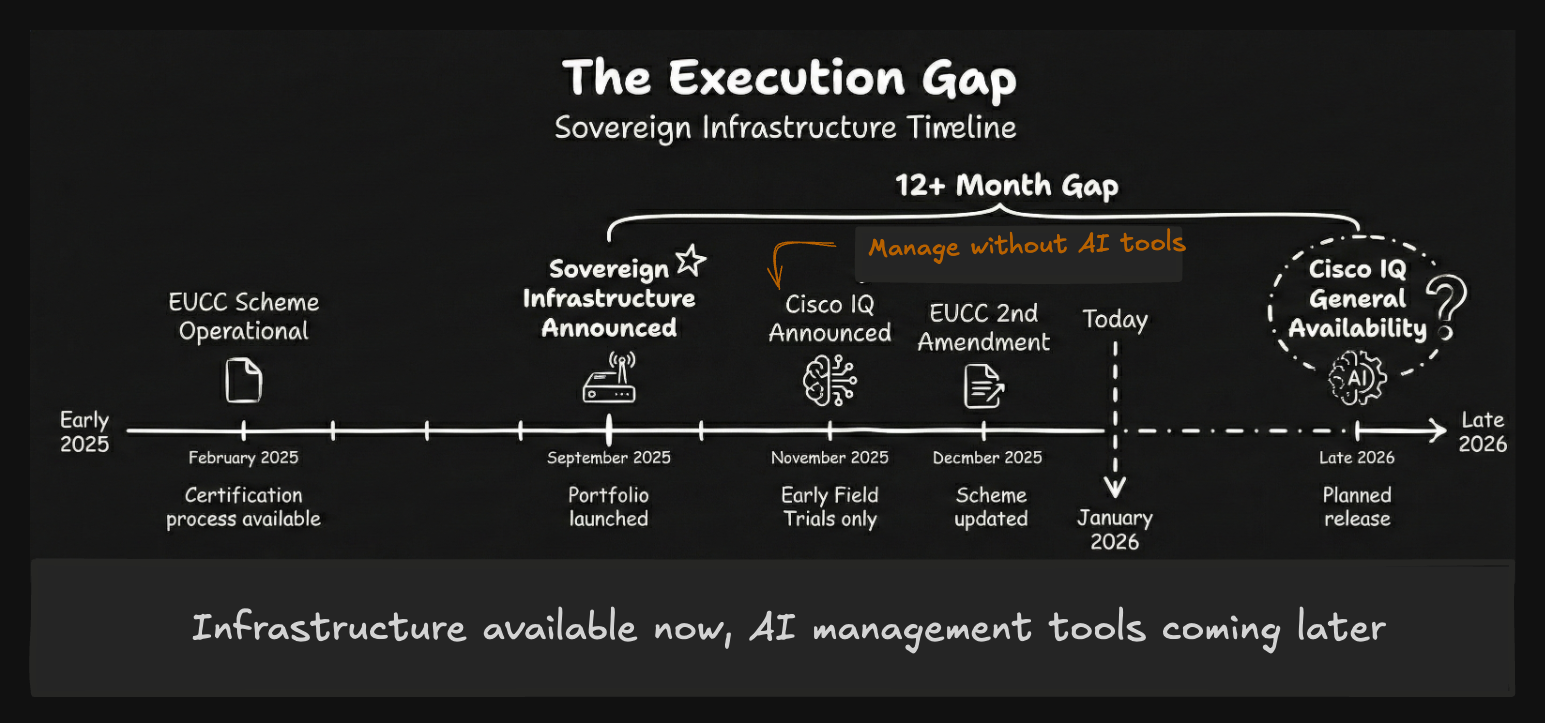
Without AI-assisted management, sovereign infrastructure at scale means choosing between Catalyst Center's automation (with manual update ingestion) or building custom tooling. Partners can fill that gap, but Cisco's value proposition weakens if their next-generation management solution isn't ready when customers need it.
Economics will determine adoption beyond government. Sovereign infrastructure is expensive—not because of price-gouging, but because the operational model is inherently costly. SLR permanently allocates licenses to specific hardware (no pooling, no flexibility). Professional services for design, hardening, and compliance documentation run 20-40% of hardware costs. Manual patching, no cloud automation, and specialized staff mean TCO substantially exceeds cloud-connected alternatives.
For government spending on classified systems, cost is secondary to control. For commercial enterprises, the calculation is different. Whether they adopt sovereign infrastructure depends on whether sovereignty becomes regulatory requirement or remains optional.
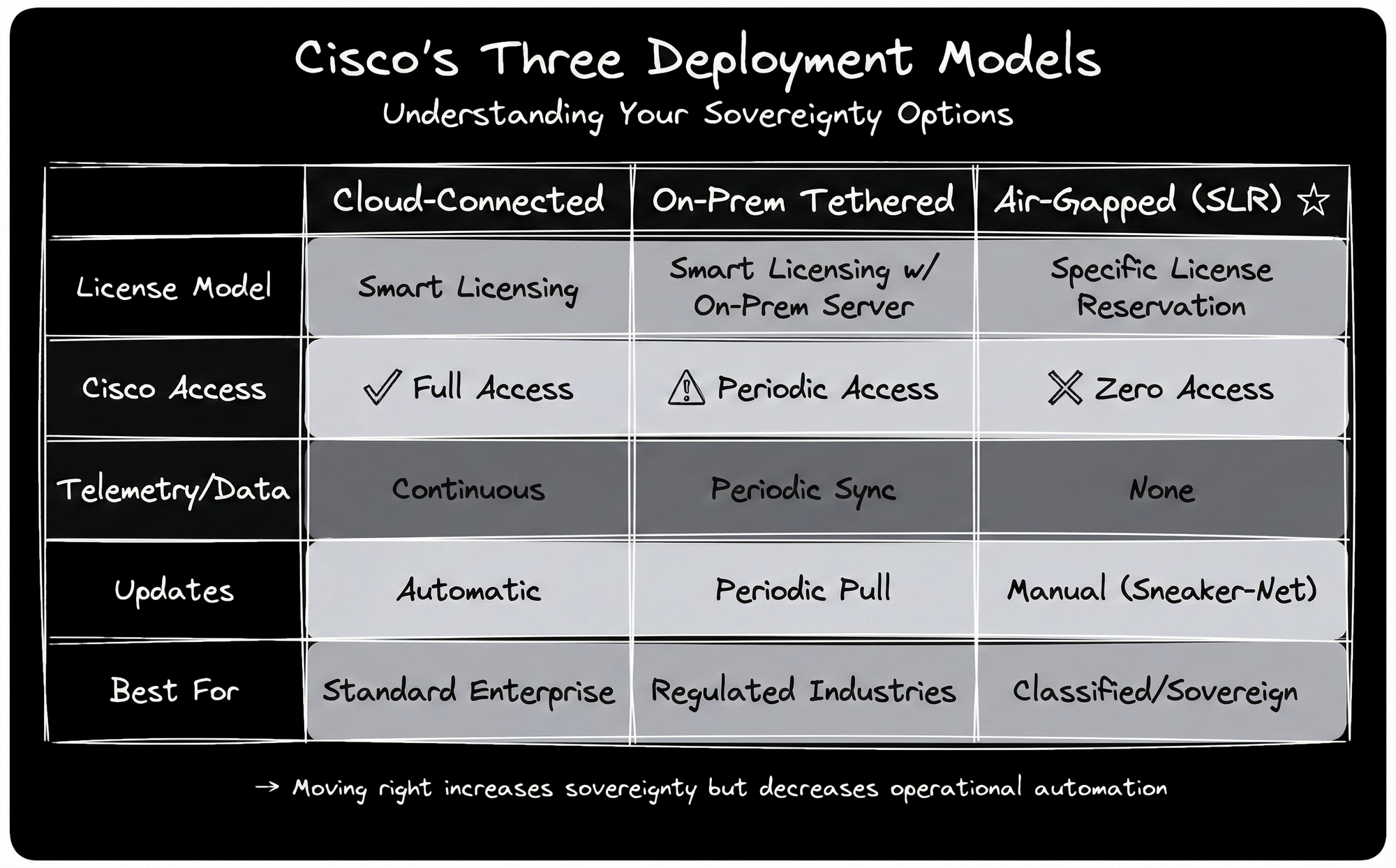
Cisco now supports three deployment models, each with different sovereignty guarantees and operational trade-offs:
What Comes Next
Five months post-announcement, proof requires actual government contracts, a scalable partner ecosystem, and concrete EUCC timelines rather than vague roadmaps.
My bet: Cisco is serious, but execution will be messier than marketing admits. The demand is regulatory-guaranteed and the tech is real, but the operational complexity of air-gapped deployments will slow things down.
Vindication or Mirage?
For specialist integrators who maintained air-gapped expertise through the cloud-first decade, September 2025 wasn't just an announcement—it was validation. The infrastructure they built when Cisco's roadmap pushed cloud? Suddenly strategic, not legacy. The professional services expertise they developed for operating without internet connectivity? Now a growth market. The certifications they obtained for classified environments? Essential, not edge cases.
Europe wants its most sensitive infrastructure truly under its control. Not "managed by EU subsidiaries." Not "hosted in EU data centers." Under control means no external entity can access, modify, or terminate operations. That requires infrastructure that doesn't phone home—by design, not workaround.
The question isn't whether demand is real. Geopolitical tensions, regulatory requirements, and AI infrastructure needs make sovereign control inevitable for critical systems. The question is whether Cisco executes.
We'll know whether Sovereign Critical Infrastructure delivers—or whether "sovereign" joins "software-defined," "intent-based," and "self-healing" in the graveyard of networking buzzwords that sounded transformative in press releases but dissolved into incrementalism in production.
For specialist integrators and their customers, stakes couldn't be higher. If Cisco is serious, on-premises expertise becomes a growth market for the first time in a decade. If it's positioning, they're back to building workarounds for cloud-first products that don't quite fit sovereign requirements.
The real test comes 12-24 months out, when we see whether initial deployments expand or stall, whether certifications materialize or remain perpetual roadmap items, and whether "sovereign infrastructure" becomes a product category or just another PowerPoint promise.
That's not a niche market. That's a multi-billion dollar infrastructure category being reborn. Whether Cisco executes perfectly or imperfectly, market demand won't wait. Governments will deploy sovereign infrastructure with or without Cisco. The question is whether Cisco positioned itself to capture that opportunity, or whether specialists build it themselves using open-source alternatives and white-box hardware.

